
Audit of the
Personal Information Management
Practices of the
Canada Border Services Agency
Trans-border Data Flows
June 2006
Office of the
Privacy Commissioner
of Canada
Commissariat à la
protection de la vie privée
du Canada

2
TABLEOFCONTENTS
SectionI MainMessages 3
SectionIIIntroduction
ContextfortheAudit 5
WhythisAuditisimportant 6
AbouttheCanadaBorderServicesAgency 7
Auditobjective,criteria,scopeandapproach 8
SectionIII–ObservationsandRecommendations
CustomsEnforcementandIntelligenceActivities
(LandBordersandAirports) 11
InformationTechnologySystemControls
IntegratedCustomsEnforcementSystem(ICES) 23
PassengerInformationSystem(PAXIS) 32
NationalRiskAssessmentCentre 38
PrivacyManagementFramework 46
PublicReportingofTransBorderDataFlows 52
AppendixA ListofRecommendations 56
AppendixBAuditEvaluationCriteria 59
AppendixC Listof Acronyms 70

3
SECTIONI
MAINMESSAGES
1.1 We foundthattheCanadaBorderServicesAgency(CBSA)hassystemsand
proceduresinplaceformanagingandsharingpersonalinformationwithothercountries.
However,significantopportunitiesexisttobetterman ageprivacyrisksandachievegreater
accountability,transparencyandcon troloverthetransborderflowofdata. Transborderdata
flowsrefertopersonalinformationthatiscollectedordisclosedacrossinternationalborders.
1.2 Writtenrequestsforassistancefromforeigngovernmentsareprocessedinaccordance
withrequirements.However,manyoftheinformationexchangesbetweentheCBSAandthe
UnitedStatesattheregionallevelareverbal,andarenotbasedonwrittenrequests.These
exchangesarenotrecordedconsistentlyanddonotfollowtheapprovalprocessasestablished
underCBSApolicy. Furthermore,theyarenotcompliantwiththetermsoftheCanadaUnited
StatesCustomsMutualAssistanceAgreementofJune1984.
1.3 TheCBSAneedsacoordinatedmethodofidentifyingandtrackingallflowsofitstrans
borderdata. TheAgencycannot,withareasonabledegreeofcertainty,reporteitheronthe
extenttowhichitsharespersonalinformationwiththeUnitedStates,orhowmuchandho w
oftenitsharesthisinformation. Byextension,itcannotbecertainthatallinformationsharing
activitiesareappropriatelymanagedandcomplywithsection107oftheCustomsActand
section8ofthePrivacyAct.
1.4 Generally,thecontrolssurroundingthePassengerInformationSystem(PAXIS)andthe
IntegratedCustomsEnforcementSystem(ICES)aresound. Thesetwokeysystemscontain
sensitivepersonalinformationaboutmillionsoftravellers. Notably,foreignjurisdictionsdonot
havedirectaccesstothesesystems,andelectronicdisclosurestotheUnitedStatesunde rthe
SharedLookoutandHighRiskTravellerIdentificationinitiativesaretran smittedoversecure
channels. However,thereareopportunitiestostrengthencontrolstofurtherreducetheriskthat
personalinformationcouldbeimproperlyusedordisclosed. Theseopportunitiesinclude:
· completingtheintroductionofanewsecuritymanagementframeworkas
initiatedbytheCBSA;
· updatingandclarifyingrolesandresponsibilitiesforITfunctions;
· ensuringsystemaccessrightsarekeptuptodate;
· implementingauditcontrolcapability forlookoutdataprintouts;and
· introducingamechanismforCanadaandtheUnitedStatestoassureeachotherthatthe
systemcontrolsandprotectionofsharedpersonalinformationareadequate.
1.5 TheCBSAneedstoexplorewaystoimprovethequalityandcontrolofdataitacquires
undertheAdvancePassengerInformation/PersonalNameRecord(API/PNR)initiativeto
ensurethatpersonalinformationisasaccurateandcompleteaspossible.

4
1.6 TheCBSAhasnotyetevaluatedtheeffectivenessoftheHighRiskTraveller
Identification(HRTI)InitiativewiththeUnitedStatesbecausetheprojecthasyettobefully
implemented. Inparticular,itshouldassesstheextenttowhichinaccurateorincompletedata
mayaffectenforcementobjectivesandindividualtravellers. UntiltheCBSAhasevaluatedthe
initiative,theAgencywillnotbeabletodemonstratethatithasachieveditsobjectiveand,
accordingly,thatthecollectionanduseofvastamountsofpersonalinformationaboutmillions
oftravellersisjustified.
1.7 TheCBSAisanewentity. Therefore,thetimeisopportunefortheAgencytoarticulate
andimplementacomprehensiveprivacymanagementframework. Inparticular,theCBSA
shouldworktowardupdatingandstrengtheningitsagreementswiththeUnitedStatescovering
the sharingofpersonalinformation.TheAgencyshouldalsoconsolidateitsreportingofprivacy
incidentsandlookforwaysofimprovingthemonitoringofpersonalinformation disclosures.
1.8 Finally,theactivitiesassociatedwithsharingdataacrossbordersshouldbemade
moretransparent. Aclearand completepictureoftheseactivitiesisnotreadilyavailableto
showwhatinformationissharedwithwhom,andforwhatpurpose. Asistrueforother
departments,theCBSA’stransborderdataflowsarenotaccountedforinmeaningfuldetail.
Moretra nsparencyisneededtobetterinformParliamentandtheCanadianpublicabout
activitiesinthisarea.
1.9 Addressingsuchmattersisinthepublicinterest.Webelievethatstrongprivacy
managementandaccountabilityareessentialfordealingwiththepublic’sconcernsaboutthe
flowofpersonalinformationfromCanadatoothercountries.

5
SECTIONII
INTRODUCTION
ContextfortheAudit
2.1 TheCanadianeconomydependsgreatlyonexchanginginformationwithpa rtners
aroundtheworld.WhileCanadahasmanytradingpartnersandallies,itsstrongesttiesarewith
itsclosestneighbour–theUnitedStatesofAmerica.
2.2 Technologicaladvancesoverthepasttwodecadeshaveremovedmanyofthe
communicationba rriersforexchanginginformation.Dataexchangesbetween multinational
companiesandnationalgovernmentshaveincreasedwiththeexpansionofdatabasecapacities
andthecreationofglobalcommunicationsystemsandnetworkstotransmitinformation.
2.3 Globalizationhascausednationstoadoptamorecooperativeandcoordinated
approachtoregulatinggoodsandpeopleand,inparticular,informationcrossingtheirrespective
borders.Thisinturnhasresultedinanincreaseinthesharingofpersonalinformationbetween
nationalgovernments–somethingthatwasgivenaddedmomentuminrelationtolaw
enforcementandnationalsecurityfollowingthetragiceventsofSeptember11,2001.
2.4 InrespondingtotheterroristattacksofSeptember11,2001,governmen tsaroundthe
world–includingtheGovernmentofCanada–introducedmeasurestostrengthennationaland
internationalsecurity. Generally,suchmeasuresseemedtobebasedonthepremisethatthe
moreinformationgovernmentshaveaboutindividuals,thesaferandmoresecuresocietywill
be.
2.5 Sincetheeventsof9/11,callshavearisenforbettersharingofinformationbetweenlaw
enforcementpartnersdomesticallyandinternationallytorespondtothethreatofterrorism.All
lawenforcementandintelligenceagenciesmustbalanceheightenedsurveillanceandsecurity
measureswithcompetingcallsforselectivesharingandgreateroversighttoensurethatcivil
liberties–includingtherightofprivacy–arenotunnecessarilycompromised. Nevertheless,
travellerswouldgenerallyunderstandthatthedegreeofpersonalprivacyataportofentryinto
Canadawillnotbethesameasmayotherwisebethecaseineverydaylife.Scrutinyofpeople
andgoodsbyCBSAofficialsistobeexpected,anditisprovidedforbylawasameansof
protectingthegeneralwelfareofCanada.According ly,screeningandinformationsharingby
the CBSAforpurposeofbordermanagementtakesplaceinageneralcontextofreduced
privacy.
2.6 WechosetheCBSAforauditafterconsideringanumberoffactors. Keycomponentsof
theGovernmentofCanada’snationalsecurityagendafocusonstrengtheningtheCanadaU.S.
border,andtheCBSAisthecentralorganizationresponsibleforbordersecurityinCanada.In
December2001,CanadaandtheUnitedStatessignedthe“SmartBorder”Declaration–the
ManleyRidgeSmartBorderDeclarationand30PointActionPlantostrengthentheshared
borderwithoutundulyrestrictinglegitimatetradeandtravel.Amainobjectiveoftheplanwas
toexploreoptionsforincreasingbilateralcooperationandtheexchangeofenforcementand
intelligenceinformationbetweenthetwojurisdictions.

6
2.7 Infulfillingitsborderprotectionmandate,theCBSAcollectssensitivepersonal
informationaboutmillionsoftravellersarrivinginCanada. Thisinformationmayincludedetailed
financial,familyhistoryandtravelinformation,aswellaspersonalidentifierssuchassocial
insuranceandpassportnumbers.Muchofthisinformationisretainedinanidentifiableformat
eitherinhardcopy(physicalfiles)orinelectronicdatabases.Thisinformationmaybe
exchangedwithforeigngovernmentsundersection107(8)oftheCustomsAct.
2.8 The“CustomsActionPlan”ofApril7,2000articulatedanewriskbasedmanage ment
approachtocustomsenforcement. ThePlanfocusedondirectingcustomsresourceswhe re
the ywouldproducethebestresults. Thisnewenforcementmethodhasledtothecollection
anduseoflargequantitiesofpersonalinformationabouttravellers,withthepotentialthatthe
informationmaybesharedacrossborders. Whenmorepersonalinformationiscollected,used
anddisclosed,correspondingprivacyrisksincrease.
2.9 Finally,theGovernmentofCanada’sNationalSecurityPolicyofApril27,2004included
newfundingforbordersecurityinitiatives,includinge xpandingtheCBSA'sintelligence
gatheringcapacityandthecreationoftheNationalRiskAssessmentCentretofacilitatethe
sharingofintelligenceandlookoutinformationwiththeUnitedStates(seeparagraph3.58fora
briefexplanationof“lookouts”).
WhythisAuditisimportant
2.10 Inanenvironmentwithinwhichnationa lgovernmentsareresponsibleforprotectingthe
privacyrightsofindividuals,andinwhich manyofthesegovernmentsoffertheircitizens
variablelevelsofprotection,thetransborderflowof pe rsonalinformationraisesuniqueprivacy
challenges.How,forexample,cantheGovernmentofCanada,withintheterritoriallimitsofthe
applicationofitslaws,ensurethatinformationitshareswithaforeigngovernmentwillbe
accordedthesamelevelofprotectionthattheinformationenjoysinCanada? Willgenerally
accepteddataprotectionprinciplesberecognizedandrespected?
2.11 Morespecifically,thisauditisimportantforanumberofreasons. First,thetransborder
flowofpersonalinformationraisesseriousinherentprivacyrisksrelating tojurisdictional
diffe rencesinpracticesaffectingtheprotectionofpersonalinformation,thesecurityofpersonal
dataintransitandtheadequacyofinstrumentsgoverningthemanagementofthepersonal
informationonceithasbeenshared.Inthisregard,weviewthetermsandconditions
establishedunderbilateralinformationsharingagreementstobeimportantelementsofthe
controlenvironmentsurroundingtransborderdataflows.
2.12 Second,thereareclearindicationsthattheCanadianpublicisconcernedaboutthe
transborderflowoftheirpersonalinformationtotheUnitedStates.Inastudycommissionedby
thisofficein2004,75%ofrespondentsbelievedthattheGovernmentofCanadatransfers
citizens’personalinformationtoforeigngovernmentsforthepurposeofprotectingnational
security,with85%ofthosesurveyedreportingamoderateorhighlevelofconcernaboutthese
transfers.Int hesamevein,manyhaveraisedtransborderconcernsaboutdatamining,racial
profiling,directaccesstoCanadiandatabasesbythe foreigngovernments(notablytheU.S.)
andsecondaryusesoftheinformation.

7
2.13 Third,aslawenforcementandnationalsecurityorganizationsaroundtheworldcollect
moreinformationfrommoresourcesaboutmoreind ividuals,andastheyusethatinf ormation
toidentifypossiblethreats,thereisaninherentriskofincompleteorinaccuratedataleadingto
undesirableconsequencessuchasunnecessaryscrutinyofindividuals.
AbouttheCanadaBorderServicesAgency
2.14 TheCanadaBorderServicesAgency(CBSA)wascreatedonDecember12,2003.
ItispartofthePublicSafetyandEmergencyPreparedness(PSEP)portfolio.TheCBSA
encompassesthecustomsprogramfromtheformerCanadaCustomsandRevenueAgency
(CCRA),theenforcement,intelligenceandinterdictionfunctionsofCitizenshipandImmigration
Canada(CIC)and theprimaryfoodandplantinspectionfunctionsoftheCanadianFood
InspectionAgency(CFIA).
2.15 TheCBSA’slegislativemandateistofacilitatethe legitimatecrossborderflowofpeople
andgoodsinsupportoftheCanadianeconomy,whileinterceptingthoseindividualsandgoods
thatposeapotentialsecurityrisktoCanadaoritsallies,orwhoarenotcomplyingwith
Canadiancustoms,immigrationandotherlaws.TheCBSAadministersmorethan90statutes
governingtradeandtravel.
2.16 Byservingasafirstlineofdefenceinmanagingthemovementofpeopleandgoods
enteringandleavingCanada,theCBSAoperatesatsome1,200servicepointsacrossthe
countryand39locationsabroad. Itispresentat119landbordercrossingsandnine
internationalairports.Overthepastfiscalyear,theCBSA’sstaffofapp roximately12,500
processedover12millionshipmentsand95milliontravellersarrivinginCanada–whetherby
land,airorwater.Inthesameperiod,theAgencyprocessedmorethan2millionpeople
referredforimmigrationreasons.
2.17 TheCBSA’sheadquartersisinOttawa. Itsoperationsaredivided intoeightregions–
Atlantic,Quebec,GreaterTorontoArea,NiagaraFalls/FortErie,Windsor/St.Clair,Northern
Ontario,PrairieandPacific.
2.18 TheCBSAhadabudgetof$1.06billiontocarryoutitsbordermandateforthefiscal
yearendingMarch31,2005. MoreinformationabouttheCBSAcanbeobtainedfromreports
publishedonitswebsiteatwww.cbsaasfc.gc.ca.
2.19 Whenwewerecarryingoutouraudit, theCBSAwasorganizingasanewentity.
Accordingly,systemsandproceduresrequiredadjustingandwerechanging. Werecognize
thatduringaperiodoftransformationthereismuchtobedone,andofficialswereworkinghard
tolearnandadapt. Atthesametime,therecanbesomeconfusionoruncertaintyamong
managementandstaffaboutrolesandresponsibilitiesandhowcorporatesystemsshouldand
dooperate. Nevertheless,itshouldalsobeunderstoodthattransborderdataflowsarecentral
tomanyoftheAgency’sprogramsandthedaytodayoperations. NeithertheAgencynorthe
federalgovernmentasawholehas,asyet, focusedontheseflowsasacollectivemanagement
andaccountabilityissue.

8
Auditobjective,criteria,scopeandapproach
2.20 Nationalsecurityandprivacyobjectivesareoftenperceivedasvaluestobebalanced
againsteachother–where,forexample,increasedsecuritymustresultinacorrespondingloss
ofprivacy.Thepremiseofthisauditisthatnationalsecurityobjectivesandsoundpersonal
informationmanagementpracticesaremutuallydependent.
2.21 Underlyingthishypothesisisthebeliefthatastronga ccountabilityandcontrol
frameworkoverthemanagementofpersonalinformationwillmitigateprivacyrisks,anditwill
alsosupportnationalsecurityandlawenforcementobject ives.Inotherwords,securitythat
respectsprivacymakesforbetter,moreeffectivesecurity.
Auditobjective:
ToassesstheextenttowhichtheCBSAisadequatelycontrollingandprotectingtheflow
ofCanadians’personalinformationtoforeigngovernmentsortheirinstitutions.
Criteria:
2.22 Detailedcriteriaweredevelopedf ortheaudit. TheseweresharedwiththeCBSAand
accepted. ThecriteriaarefoundinAppendixB(page59). Inestablishingtheauditcriteria,
referencewasmadeto:
· therelevantauthoritiesoftheCustomsAct(e.g.,section107);
· thecollection,use,disclosure,retentionanddisposalprovisionscontainedin
sections4to8ofthePrivacyAct;
· the teninternationallyrecognizedfairinformationprinciplesembodiedin
Schedule1ofthePersonalInformationProtectionandElectronicDocumentsAct
(PIPEDA);and
· TreasuryBoardpolicies,guidelinesanddirectivesrelatingtothemanagementof
personalinformation.
Scope:
2.23 DuetothesizeandcomplexityoftheCBSAanditscurrentstateofreorganization,
ourauditbeganwithascopingreviewoftheAgency’smanyprogramsandinformation
managementactivities.Wecarriedoutthisexercisetoidentifytheprogramareaswherethe
impactonindividualprivacyofCanadianswouldlikelybehighestsoastodirectourattention
accordingly.Mindfulofouravailableauditresources,scopingactivitiesweredirectedatthe
managementofpersonalinformationaboutindividualtravellersratherthanattheCBSA’s
commercialprogramsandactivities.Inaddition,wefocusedoncustomsenforcementand
intelligenceactivitiesatlandbordersandairports.Thescopeoftheexaminationdidnotinclude
theAgency’smarine,railandpostaloperations.
2.24 Ourscopingactivitiesledustoselectthefollowingfourprogramareasandinformation
systemsforauditexamination:
§ Customsenforcementandintelligenceactivities(landbordersandairports);
§ theIntegratedCustomsEnforcementSystem(ICES);

9
§ thePassengerInformationSystem(PAXIS);and
§ theNationalRiskAssessmentCentre(NRAC).
2.25 Inadditiontothesefourareas,theauditexaminedtheCBSA’sprivacymanagement
framework,aswellastheextenttowhichtheAgencyreportsitsactivitiesintheareaoftrans
borderdataflowstoParliamentandtheCanadianpublic.
2.26 Althoughimmigrationenforcement,intelligenceandinterdictionactivitiesalsoinvolvethe
transborderflowofpersonalinformation,theorganizationalchangesrequiredtofacilitatethe
integrationoftheseactivitiesintotheCBSAhadnotbeenfinalizedatthetimeofouraudit.This
alsoappliestotheprimaryfoodandplantinspectionprogramthatwastransferredtotheCBSA
fromtheCFIA.Theseareaswere,therefore,notexaminedaspartoftheaudit.
2.27 Further,wedidnotreviewtheNEXUSprogram.Thisprograminvolvesextensive
backgroundscreeningtofacilitateacceleratedentryintoCanadaandtheUnitedStatesfor
approvedtravellers. EnrolmentintheNEXUSprogramisvoluntary. Moreover,thecollection,
useanddisclosureofpersonalinformationundertheprogramoccurwiththeexpressedconsent
oftheparticipant.
2.28 Asafinalnote,thePrivacyCommissionerdoesnothavejurisdictionoutsideCanada.
Therefore,wedidnotauditthecontrolanduseofpersonalinformationonceithadcrossedthe
CanadaU.S.borderintotheUnitedStates.
Approach:
2.29 Wecarriedoutinterviewswith108CBSAstaffmembers.Theintervieweesincluded
seniormanagersandprogramofficersatCBSAHeadquarters,managersandstaffof
theNationalRiskAssessmentCentre,regionaldirectors,divisionalchiefs,customs
superintendents,customsofficers,regionalintelligenceofficers,regionalintelligenceanalysts
andregionalcustomsinvestigatorsinthethreeregionsvisitedduringtheaudit–Quebec,
WindsorSt.ClairandPacific.
2.30 Inadditiontointerviewingselectedpersonnel,theauditteamexaminedasampleof
custo msenforcementrecords(e.g.,seizurereports),intelligencemanagementsystem(IMS)file
entries,officernotebooks,requestsforassistancefilesandCanadaU.S.sharedlookouts. As
the CBSAdoesnotcurrentlyhavethecapacityto readilyidentifyallfilescontainingtransborder
exchanges–specificallythosethat containinformationthathasbeenthesubjectofa verbal
disclosure–theauditteamwasunabletorandomlyselectcertaintypesoffilesforreview.
Rather,wehadtorelyuponprogramofficialstopresentrecordsforourexamination,the
selectionofwhichwasbasedonoff icers’recollectionofspecificcasesandmanualsearchesof
the irrespectiverecords(e.g.,notebooks).
2.31 Theauditteamalsoreviewedmemorandaofunderstanding(MOUs)andtreatiesthat
establishtheframeworkfordisclosing(i.e.,releasing)customsinformationtoforeign
governments,internalpoliciesandprocedures,trainingmaterials,privacyimpactassessments
andtheCBSA’sreportinginstruments(e.g.,ReportsonPlansandPriorities).
2.32 OurfieldexaminationoftheCBSAwassubstantiallycompletedbyNovember2005.
Therefore,theobservationsandrecommendationscontainedinthisreportareeffectiveasof
thatdate.

10
2.33 Aspartofourapproach,anexterna lAuditAdvisoryCommitteewasestablished.This
fou rpersoncommitteebroughtextensiveexpertiseintheareasofprivacy,lawenf orcement,
informationtechnologysecurityandpublicadministration.TheCommitteeprovidedguidance
anddirectionatvariousstagesoftheaudit.
2.34 Afterwehadcompletedtheexaminationphaseoftheaudit,weprovidedverbalbriefings
ofourfindingstomanagementoftheCBSA. DraftsofourreportwerereviewedbyCBSA
officialstoensurefactualaccuracyandtoobtainresponsestoourobservationsand
recommendations.
2.35 Someofourauditobservationsrelatetomattersthatareparticularlysensitiveinnature
andhavebeenexcludedfromthispublicreportintheinterestofmaintaininginformationsecurity
oftheCBSA.Theobservationsandrecommendationshavebeenreportedseparatelytothe
CBSAbymanagementletter.WewillbemonitoringtheAgency’seffortstoaddressthese
mattersaspartofourfollowuptothisauditreport.
2.36 WewishtothankCBSAofficialsforthe ircooperationduringtheauditandtheir
receptivenesstoourwork.
Organizationofthisreport
2.37 SectionIIIofthisreport,–ObservationsandRecommendations–followsandcovers
thefourprogramareasandinformationsystemsnotedearlier:customsenforcementand
intelligenceactivities(landbordersandairports);theIntegratedCustomsEnforcementSystem
(ICES);thePassengerInformationSystem(PAXIS);andtheNationalRiskAssessmentCentre
(NRAC). Foreach,asappropriate,weprovidesomebackgroundorbrieflydescribethe
program,initiativeorsystem. Then,observationsrelatingtothetransborderflowofpersonal
informationanddisclosuretoforeigngovernmentsarediscussedunderseparatesubheadings.
Finally,wepresent therecommendationsassociatedwithagivensetofobservations.
Auditteam
TrevorShaw–DirectorGeneral,Audit&Review
TomFitzpatrick
Michae lFagan
Robe rtBedley
Doug lasMarshall
ExternalAuditAdvisoryCommitteeMembers
JohnL’Abbe SecurityStrategistConsultant,L’AbbeConsultingServices
(FormerAssistantCommissioner,RCMP–Retired)
JohnHopkinson ITSecurityConsultant
EWAInformation&InfrastructureTechnologies,Inc.
DavidFlaherty PrivacyandInf ormationPolicyConsultant
(FormerInformationandPrivacyCommissionerofBritishColumbia)
DenisMorency IndependentPrivacyConsultant
(FormerDirectorGeneral,InformationandPrivacyCommissionerof
Quebec)
11
SECTIONIII
OBSERVATIONSandRECOMMENDATIONS
CUSTOMSENFORCEMENTANDINTELLIGENCEACTIVITIES
(LANDBORDERSANDAIRPORTS)
Back ground
3.1 ThekeycomponentsoftheCBSA’senforcementpresencearetheinvestigations,
intelligenceandinterdictionprogramsdesignedtoaddresssuspectedcasesofdutyevasion,
smuggling,fraud,terrorism,moneylaunderingandotheroffencesagainstlawsthattheAgency
enforces.
3.2 TheEnforcementBranchatCBSAHeadquartersisresponsiblefordevelopingnational
procedures,strategiesandoperationalpoliciesrelatedtotheAgency’senforcementprogram.
Otherresponsibilitiesinclude:
· collecting,analyzinganddisseminatingintelligenceregardingthreatstothe
securityofCanada’sborders;
· providingfunctionaldirectionandsupporttoCBSAfieldstaffatportsofentry
andinlandoffices;
· providingafocalpointfortheCBSA’srelationswithdomesticandforeign
security,lawenforcementandintelligencecommunities;and
· developingandmanagingnewprogramswithinternationalpartners.
3.3 TheBranchisorganizedintofourDirectorates–Enforcement,IntelligenceandRisk
Management,PolicyandProgramDevelopment,andManagementServices.WhileCBSA
Headquartersprovidespolicyandfunctionaldirectiontothefield,theresponsibilityfordelivering
the enforcementprog ramresidesattheregionallevel. TheCBSA’sregionalheadshave
managementoversightofthebordersecurityandintelligenceoperationsoftheirrespective
jurisdictions.
3.4 Enforcementoperationsincludemanagingair,landandseaportsofentryforthe
movementoftravellersandgoods.Althoughtheorganizationalstructuremayvaryslightly from
regiontoregion,theenforcementprogramsallcontainthesamegeneralcomponents–thatis,
intelligence(customsandimmigration),investigations(customsfraud)andimmigration
enforcement.
Personalinformation
3.5 TheCustomsActdefines“customsinformation”asinformationofanykindandinany
formsthat:
(a) relatestooneormorepersonsandisobtainedbyoronbehalfoftheMinisterforthe
purposesoftheCustomsActortheCu stomsTariff;or
(b) ispreparedfrominformationdescribedinparagraph(a).

12
3.6 Bydefinition,customsinformationisbroadinscope.Whilenotexhaustive,thefollowing
representsasamplingofthetypeofpersonalinformationthattheCBSAcollectsand,by
extension,couldpotentiallybethesubjectofatransborderdisclosure:
biog raphicalinformation–name,dateandplaceofbirth;
addressandtelephonenumbers(home,cellular);
previouscustomsviolations;
intelligence–methodsofconcealmen t,modusoperandioftheindividual,
commoditydatapertainingtogoodslikelytobesmuggled ,travelhistoryand
surveillancenotes;and
otherinformationsuchasvehiclelicencenumber,advancepassengerinformation
(API),passengernamerecord(PNR),employmentandfinancialinformation.
Transborderflowofpersonalinformation
3.7 Incarryingoutitsborderprotectionmandate,theCBSAcollectspersona linformation
fromavarietyofsources.Inadditiontodirectcollection–thatisfromthepersontowhomthe
informationrelates–theCBSAcollectsinformationfromaircarriers,othergovernment
departmentsandagen cies,domesticlawenforcementandintelligenceagencies,andforeign
governmentsandtheirinstitutions. Italsoreceivesinformationfrommembersofthe general
publicthroughatollfreetipline.
3.8 TheCBSAmayalsocollectinformationthroughleadsthatoriginatefromcustomsports
ofentry,surveillanceactivities,humansourcesandtheexecutionofwarrants.Inaddition,the
CBSAhasaccesstoinformationcontainedinanumberofexternaldatabases. Theseinclude
theCanadianPoliceInformationCentre(CPIC);FieldOperationalSupportSystem(FOSS)–a
CitizenshipandImmigrationCanadadatabase;thePoliceInformationReportingSystem(PIRS),
whichisbeingreplacedwiththePoliceReportingandOccurrenceSystem(PROS);andthe
U.S.NationalCrimeInformationCentre(NCIC),theU.S.equivalenttotheCanadianCPIC
system.
3.9 PersonalinformationcollectedundertheCBSA’scustomsenfo rcementprogramis
retainedinhardcopy(paper)andelectronicformats.InadditiontothePAXISandICES
applications(examinedaspartoftheaudit),enforcementpersonnelmay,dependingontheir
roleandareaofresponsibility,usethefollowingsystemsincarryingouttheirduties:
OccurrenceReportingSystem(ORS) – anelectronicreportingsystemfortransmitting
informationfromcustomsinspectorsto
intelligencepersonnel,
IntelligenceManagementSystem(IMS) – the repositoryforallintelligencedata,withaccess
beingrestrictedtointelligencepersonnel,
CustomsInvestigationsInformation – acasemanagementtrackingsystemusedby
ManagementSystem(CIIMS) investigationsstaff,whichcapturescasesummary,
tombstonedata(name,address,DOB),dateofport
prosecution.

13
Disclosuretoforeigngovernments
3.10 Subsection107(8)oftheCustomsActpermitsthedisclosureofcustomsinformationtoa
foreigngovernment,aninternationalorganizationestablishedbythegovernmentofstates,a
communityofstates,oraninstitutionofanysuchgovernmentororganization. Anyreleaseof
informationmustbe:
· inaccordancewithaninternationalconventionoragreement,orotherwritten
arrangementbetweentheGovernmentofCanadaorinstitutionthereofandthe
foreigngovernment,internationalorganizationorcommunityofstates;and
· solelyforthepurposessetoutinthearrangement.
3.11 Internationalinformationsharingagreementsdonothavetodealexclusivelywiththe
exchangeofcustomsinformation. However,theymustallowforthedisclosureorexchangeof
suchinformation.
3.12 Manybilateralagreementsbetweencustomsagenciesindifferentcountriesare
designedtoestablishprotocolsgoverningtheirmutualassistanceandcooperation.Canada
has20internationalwrittencollaborativearrangements.Sixofthesearrangementsare
CustomsMutualAssistanceAgreements(CMAA).ACMAAmustberatifiedbyOrderin
Council,hastreatystatusandisenforceableinlaw. Suchagreementsaregovernmentto
government.CanadahasaCMAAwiththeUnitedStatesofAmerica,Mexico,SouthKorea,
EuropeanUnion,FranceandGerman y.Theremainingwrittencollaborativearrange mentsare
betweenCustomsAdministrations.
3.13 CanadahasalsoenteredintoMutualLegalAssistanceTreaties(MLATs)with31
countries.ItshouldbenotedthatMLATsgoverntheoveralllegalassistanceincriminalmatters
betweencountries. ThereforetheyarenotpersethesoleresponsibilityoftheCBSA;theyare
managedjointlywiththeDepartmentofForeignAffairsandInternationalTradeandJustice
Canada.
3.14 Theofficialsauthorizedtoapprovethereleaseofcustomsinformationundertherelevant
authoritiesofsection107oftheCustomsActareidentifiedinCBSApolicyandguidelines.
CertainagreementsgoverningthesharingofinformationbetweenCanadaandtheUnited
Statescouldbestrengthenedtoprovidestrongerdataprotectionsafeguards.
3.15 TheexistingCMAAandMLATbetweenCanadaandtheUnitedStatesarelongstanding.
Inourview,theyneedtobeupdated.Moreimportantthanthefactthattheyrefertocustoms
agenciesthatnolongerexististhattheseagreementsdonotadequatelyaddressthe
managementofpersonalinformation. Thisviewisreinforcedthroughanexaminationof
CMAAswithothercountriesthatdocontainenhanced safeguardsforprotectingdata. However,
eventheseagreements,whilemoreacceptable,couldbeimproved.
3.16 TheAgreementbetweenCanadaandtheUnitedStatesestablishingmutualassistance
andcooperationbetweentheirrespectivecustomsadministrationswassignedonJune20,
1984.TheCMAAdefines“customsadministration”inCanadaastheDepartmentofNational
Revenue,CustomsandExcise.Theageoftheagreementisevidencedbythefactthatthis
departmenthasbeensucceededsincebytheCanadaCustomsandRevenueAgency(CCRA)

14
and,morerecently,theCBSA.Similarly,theUnitedStatescustomsadministrationisdefinedas
theUnitedStatesCustomsService,DepartmentofTreasury.TheCustomsServiceisnow
largelypartoftheU.S.CustomsandBorderProtectionAgency,withintheDepartmen tof
HomelandSecurity.
3.17 TheexistingCMAAbetweenCanadaandtheUnitedStatesstipulatesthatrequests for
informationmustbeinwritingandinclude:
theidentityoftheauthoritymakingtherequest;
thenatureoftheinvestigation;
thenamesandaddressesofthepartiestowhomtherequestrelates;
adescriptionofthesubjectoftherequestandthelegalissuesinvolved;and
theobjectofandreasonfortherequest.
3.18 Itshouldbenotedthatwhilerequestsforcustomsinformationmustbeinwriting,thereis
anexceptionforurgentrequests,i.e.,wherepressingcircumstancesexist.Theagreement
requiresonlythatverbalrequestsforassistancebeconfirmedinwritingattherequestofthe
otherparty.Theagreementalsostatesthatdocuments,information ,andcommunicationsare
tobekeptconfidentia landgrantedtheprotectionfromdisclosureunderthelawsofthe
receivingparty.Further,theuseofdocuments,informationandcommunicationsforany
purposeotherthanthosecontainedintheagreementrequiresthepriorwrittenconsentofthe
othercustomsadministration.
3.19 Asnotedearlier,ourauditincludedacomparisonanalysisofanumberofCMAAsthat
Canadahasenteredwithothercountries.UsingtheCMAAbetweenCanadaandtheEuropean
Union(EU)asanexample,thisagreement–whichcameintoeffectin1997–devotesmore
attentiontopersonalinformationhandlingandgenerallyprovidesbetterdataprotections
thandoestheCMAAbetweenCanadaandtheUnitedStates. UnliketheCanadaU.S.CMAA,
theCanadaEUagreementprovidesthat,whileaverbalrequestmaybemadeincertain
circumstances,thereisarequirementthatsucharequestbeconfirmedinwriting.The
agreementbetweenCanadaandtheEUalsoincorporatesthe“needtoknow”principle–that
is,thedisseminationofinformationamongcustomsauthoritieswitheachcountryshalloccur
onlyonaneedtoknowbasis. Theagreementalsorestrictscommunicationsregarding
requeststospecificallydesignatedofficials.
3.20 Further,Article16oftheCanadaEUCMAAprovidesthatsharedinformationshallbe
treatedasconfidential. Italsorequiresthatinformationprovidedbesubjecttothesame
protectionaffordedbynotonlythelawsofthereceivingcountry,butalsothelawsofthecountry
thatprovidedtheinformation.ThismeansthatinformationCanadaprovidestoanEUcountry
mustbetreatedinaccordancewithbothCanadianprivacylawsandthelawsoftheparticular
EUcountry.
3.21 SimilartotheCMAAbetweenCanadaandtheU.S.,theCanadaEUagreementalso
statestheinformationcannotbeusedforpurposesotherthanthosespecifiedintheagreement
withoutpriorconsent.However,inaddition,Article16furtherstipulatesthatsuchsecondary
usemaybesubjecttoanyrestrictionsestablishedbythecountryprovidingtheinformation.

15
3.22 TheMutualLegalAssistanceTreaty(MLAT)betweenCanadaandtheUnitedStates
wassignedinMarch1985. Requestsforassistanceunderthe MLATmustinclude,among
otherthings,thesubjectmatteroftheinvestigation,adescriptionofandthepurposeforwhich
theinformation,evidence,andassistanceissought,andanyrequirementsforconfidentiality.
Unlessotherwiseauthorizedbytherequestingcountry,therespondingcountryisrequiredto
useits“bestefforts”tomaintaintheconfidentialityofrequestsandtheircontents.The
agreementalsostatesacountrymayrequireinformatio nbekeptconfidentialorthatitbe
disclosedorusedsubjecttocertainrestrictions. Inaddition,therequestingcountryisprohibited
fromusingordisclosinginformationprovidedforpurposesotherthanthosecontainedinthe
requestwithoutpriorconsent.
3.23 OurauditincludedareviewofotherMLATs,includingtheMLATbetweenCanadaand
GermanyofOctober2004.W hencomparedtotheCanadaU.S.treaty,theCanadaGermany
MLATprovidesadditionalsafeguardsoveranyinformationthatmayberequested. These
safeguardsrequirethatrequestsforinformationinclude:
· theidentityofpersonswhoaresubjectofinvestigationand,wherepossible,a
listofquestionsanddetailsofanyrightofthatpersontorefusetogiveevidence;
· adescriptionoftheallegedoffenceandastatementoftherelevantlaw;and
· thesubjectmatteronwhichindividualsaretobeexamined.
3.24 TheCanadaGermanyMLATalsoprovidesthattheuseofpersonalinformationshared
bywayofthetreatyislimitedtothepurposesforwhichitistransmitted,totheprevention
andprosecutionofoffencesrelatedtothetreaty,torelatedcivilcourtandadministrative
proceedings,andtoavoidsubstantialpublicsecuritythreats.Anyotheruserequirestheprior
consentofthecountrytransmittingtheinformation.
3.25 Unde rthesameMLATthereceivingcountrymustinformthetransmittingcountryof
anysecondaryusemadeoftheinformation.Bothpartiesmusthandletheinformationcarefully
andensurethattheinformationtheyprovideisaccurateandcomplete.Ifonepartyisaware
thattheinformationithasprovidedisinaccurate,itmustadvisetheothercountry,whichisthen
responsibleforeithercorrectingtheinformationorreturningit. Theexchangeofinformationis
limitedtothatrelatedtotherequest.Partiesmustmaintainanappropriaterecordofthe
transmissionandreceiptofpersonalinformationandprotecttheinformationfromunauthorized
access,alteration,ordisclosure.
3.26 Onlyoneoftheagreementsthatwereviewedrequiresthattheprocessesforhandling
personalinformationbesubjecttoaudit. Auditingtheseprocesseswouldallowforreciprocal
assurancebetweenthetwocountriesthatthesignatoriesareadheringtothetermsand
conditionsoftheagreements. TheMOUfortheAutomatedExchangeofLookoutsandthe
ExchangeofAdvancePassengerInformation–signedinMarch2005–requirestheparticipants
toensurethatapprop riateauditingandtrackingmechanismsareinplacetosafeguard
information.However,theMOUdoesnotestablisharequirementfortheagenciestoshare
the auditresultswiththeotherpartytoprovideassurancesthattheobligationsundertheMOU
arebeingmet.

16
3.27 Webelievetheideaofreciprocalormutualassuranceregardingprivacytobeimportant
notonlyforinformationaboutCanadiansthatissharedwiththeU.S.,butalsoforAmericans
whosepersonalinformationmaybesharedwithCanada. A systemofmutualassurancecould
includeeachcountryprovidinginf ormationtotheotherdetailingtheinternalcontrolsadoptedin
eachjurisdictionforprotectingpersonalinformation. Thesystemcouldalsorequiretheparties
tocarryoutinternalprivacyandsecurityauditsandsharetheresults. Thesepracticeswould
alloweachcountrytoprovideassurancetotheotherwithrespecttoitsregimeforprotecting
data. Theymightalsoenablethepartiestohelpeachothe rfollowsounddataprotection
principlesandpractices.
Recommendation#1:
ItisrecommendedthattheCBSA,aspartofstrengtheningitsprivacymanagement
framework,seektoupdateandstrengthenitspersonalinformationsharingagreements
withtheUnitedStates,includingtheestablishmentofprocessesthatprovidemutual
assurancethattransborderedpersonalinformationisaccordedappropriateprotections.
CBSAResponse:
Inthenearterm,theCBSAwillcreateaPrivacyManagementFrameworktoguidepolicy
developmentandconsideraplantoupdateexistingCustomsMutualAssistance
Agreements(CMAAs). CBSAwillconsidertheelementsofthePrivacyManagement
Frameworkalreadyinplaceandwillworktoclarifyrolesandresponsibilitiesrelatedto
Privacy.Wearedevelopingguidelinesonthedevelopmentofwrittencollaborative
arrangementsthatreflectadviceprovidedbytheOfficeofthePrivacyCommissioner
(OPC). Inthelongterm,guidelineswillberevisedtoprovidedirectionontheaccess,
useanddisclosureofpersonalinformationtoforeigngovernments.
Writtenrequestsforassistancefromforeigngovernmentscontaintherequiredelements
establishedunderCustomsMutualAssistance Agreements(CMAAs)andtherequests
wereprocessedinaccordancewithSection107(8)oftheCustomsActandCBSApolicy.
3.28 Theresponsibilityforrespondingtorequests fromothercountriesforassistanceunder
CMAAsrestsprimarilywiththeCBSA’sEnforcementBranch. Dependinguponthenatureofthe
assistancebeingsought,eithertheCustomsInvestigationsDivisionortheIntelligenceand
ContrabandDivisionprocesstherequest. Withtheexceptionofrequestsoriginatingfromthe
UnitedStates,allforeignrequestsforassistanceunderCMAAsarecoordinatedthroughCBSA
Headquarters.
3.29 InNovemberDecemberof2003,theCanadaCustomsandRevenueAgency(CCRA)
issuedinterimope rationalguidelines, InterimMemorandumD1161andD1162.Inadditionto
providingaclausebyclausedescriptionofsection107oftheCustomsAct,theguidelines
providedirectionforusingcustomsinformationwithintheAgency. Theyalsocoverthe
disclosureofsuchinformationtoexternalorganizations,bothdomesticandforeign.The
Memoran dasupplementtheinformationfoundintheCBSA’sCMAAsandMLATs.

17
3.30 Memoran dumD1162identifiestheoff icialsauthorizedtodisclosecustomsinformation
underthevariousclausesfoundinsection107oftheCustomsAct.ThisMemorandumhasnot
beenmodifiedsincetheCCRAcreatedit,andtheauditteamwasinformedthatitsprovisions
remainineffectasCBSAoperationalpolicy.
3.31 Asdiscoveryorexploratorysampling,weexamined80internationalassistancefiles.
Whileourexaminationfocusedonthetransborderflowofpersonalinformationbetweenthe
CBSAandtheUnitedStates,italsoincludedasampleofrequestsfromotherforeign
governments. Ourexaminationofthewrittenrequestforassistancefilesconfirmedthatallof
theinformationexchangeshadbeenapprovedbyofficialswhohadthedelegatedauthority
underCBSApolicy. Weconcludethatthisbasicaspectofinternalcontrolisworkingwell.
3.32 Thedocumentationcontainedinthesampleestablishedtheauthorityunderwhichthe
requestshadbeenmade,thenatureoftheinvestigation thattheforeigncustomsagencywas
carryingout,andtheexactnatureofthedisclosure.Wearesatisfiedthattheexchangesof
informationwerepermittedundertheapplicableCMAA,section107(8)oftheCustomsAct,and
thatthedisclosuresmadebytheCBSAwerelimitedtotheinformationthatwasnecessaryto
complywiththerequests. ThereviewalsofoundnoincidencesinwhichtheAgencyhad
disclosedinformationfromexternaldatabases–suchasthePoliceInformationReporting
System(PIRS)ortheCanadianPoliceInformationCentre(CPIC)–toathirdparty. Wenote
thatsuchinformationcanbereleasedonlywiththepermissionoftheorganizationwhich
controlsthatinformation.
Theaccountabilityframeworkandcontrolenvironmentsurroundingverbalcrossborder
exchangesofpersonalinformationneedtobestrengthened.
3.33 Ourauditexaminedtheexistinginstruments–informationsharingagreementsand
CBSApolicies–thatgoverncrossborderexchange sofpersonalinformation. Ourobservations
relatetothelevelofcompliancewiththeaccountabilityframeworkcontainedinthese
instruments. Itshouldbenotedthatourauditdidnotincludeassessingtherelativemeritsof
therequirementsundertheexistingCMAAbetweenCanadaandtheUnitedStates,including
therequirementthatexchangesofinformationbeprecededbyawrittenrequestunlessurgent
circumstancesexist.
3.34 Ingeneral,ourobservationsshowedthefollowing:
· Inmanyinstances,theCBSAhasdisclosedinformationtotheU.S.withouta
writtenrequestf romthatcountry.
· Informationisof tendisclosedwithoutfirstobtainingapprovalfromadesignated
CBSAofficial,whichcontravenestheAgency’spolicy.
· Wefoundweaknessesintherecordkeepingassociatedwithdisclosu resof
information.
3.35 Rega rdingthereleaseofinformationwithoutawrittenrequest,weinterviewedselected
managersandregionalintelligenceofficers(RIOs)withintheIntelligenceandContraband
Divisionsthatwevisited. TheytoldusthatmanyexchangesofinformationwiththeU.S.occur
attheregionallevelwithoutawrittenrequest,contrarytotheexistingCanadaU.S.CMAA. Of
the22RIOswhomweinterviewed,approximately64%or14acknowledgedthattheydoshare

18
custo msinformation–includingpersonalinformation–verballywiththeirU.S.counterparts.
OftheeightRIOswhoreportedno involvementincrossborderverbalexchanges,sixwerefrom
thesameregion. Theseofficersexplainedthattheirspecificroleandareaofconcentration
meantthattheywerenotinvolvedinverbalexchangeswithU.S.authorities. Duringfollowup
meetingswiththreemanagersofthisregion,theauditteamwasinformedthatRIOsmayshare
informationwiththeU.S.Onemanage rdescribeddailyexchangesbetweensomeRIOsand
theU.S.asbeingverbalinnature80to95%ofthetime.
3.36 ThefrequencyofverbalcontactwiththeU.S.variedamongthe14RIOswhoreported
involvementincrossborderexchangesofinformation,andwasdependentinlargepartupon
the irspecificroleandlocation.Whiletheestimatesvaried,approximatelyonehalfofthe
respondentsindicatedthatverbaldisclosuresrepresentedbetween7090%oftheirexchanges
withU.S.customsauthorities,andcouldincludethefollowinginformation:
anindividua l’spassageortravelhistory;
ageneralsynopsisofpreviousenforcementactions;
confirmationoftheexistenceofafileheldbytheCBSA;
confirmationoftheexistenceofafilewithanotherlawenforcementagency.
3.37 Intermsoftheextentofverbalsharing,theauditteamwasinformedthatanexchange
wouldnotoccurifitcouldeitherpotentiallycompromiseongoinginvestigativeandintelligence
activities,identifyaconfidentialsourceofinformation,orrevealinformationthatanexternal
organization(thirdparty)hadsuppliedtotheCBSA.
3.38 Withoneexception,theRIOsreportedthatawrittenrequestwouldberequiredpriorto
releasingdocumentationtotheU.S.Usingtheexampleofapreviousenforcementaction,the
auditteamwasinformedthatwhilegeneraldetailssurroundingacustomsseizuremightbe
sharedverbally(theexceptionbeingseizuresinvolvingcurrency),awrittenrequestwouldbe
requirediftheU.S.wishedtoobtainacopyoftheseizurereportandsupportingdocumentation.
3.39 We alsointerviewed10customsinspectorsandfourcustomssuperintendentsatthe
landbordercrossingsthatwevisited. Ofthese,6 ofthe10inspectorsandtwoofthe four
superintendentsindicatedthattheyhave(althoughrarely)sharedtheresultsofnameand
vehiclequerieswithU.S.borderprotectionofficers. Wenotethatvehiclecrossinginformation
representedthemajorityofsuchdisclosures.Intermsofairportoperations,weinterviewed
eightcustomsinspectorsandthreesuperintendents. Nonereportedinvo lvementinexchanges
ofinformationwiththeU.S.Itwasexplainedthatrequestsforassistanceoriginatingfromthe
U.S.arereferredtotheRIOonsite.
3.40 Withrespecttotheprocessforapprovingrequestsforinformation,underits D1161
andD1162Memoranda,theCBSAhasidentifiedanddesignatedspecificofficialswiththe
authoritytoapprovedisclosuresofinformationunderthevariousprovisionsofsection107of
the CustomsAct.Thispolicyrequiresthatadesignatedofficialmustautho rizethereleaseof
informationtoathirdparty. Theexceptionisifurgentorimminentcircumstancesexist(e.g.,the
releaseofinformationisnecessarytoprotectlife,healthorsafetyofanindividual)andprior
approvalcannotbeobtained. Allsuchexceptionsaretobereportedtoadesignatedofficialas
soonaspossibleaftertheevent.

19
3.41 Attheregionallevel,theauthoritytoreleasecustomsinformationtoforeigngovernments
hasbeendelegatedtotheManager/Directorofacustomsprogramarea.Theauditfoundalow
levelofcompliancewiththepolicy. Inmanyinstances,informationissharedverballywithU.S.
custo msofficialswithoutpriorapproval. Althoughtherewereexceptions,theRIOsinvolvedin
exchangeswiththeU.S.generallyacknowledgedthatverbalexchanges–disclosuresin
responsetoaU.S.requestforassistanceandongoingexchangesthatrelatetofilesofcommon
interest–occurwithoutpriorapprovalfromtheManager/Director. Similarly,thecustoms
inspectorswhoreportedsharinginformationwiththeirU.S.counterpartsconcededthatsuch
exchangestakeplacewithoutobtainingpriorauthorizationfromamanager.
3.42 Inourview,alackofcompliancewiththepolicyunderminesboththeAgency’soverall
controlandaccountabilityframework,anditsabilitytoeffectivelymonitoritsinformationsharing
practiceswithforeignentitiestoensurethattheycomplywiththerequirementsoftheCustoms
ActandthePrivacyAct.
3.43 Asnotedabove,wefoundweaknessesintherecordkeepingrelatingtoreleasesof
personalinformation. Anindividual’srighttoprivacyincludestherighttoknowwhatpersonal
informationgovernmentinstitutionscollect,underwhatcircumstancesthisinformationmaybe
sharedwithathirdparty,andwithwhomitwillbeshared.Infulfillingthisobligation,itis
essentialthatinstitutionscreateandretainrecordsrelatingtoalldisclosuresmadetoexternal
organizations.
3.44 Unde rCBSApolicy,officialsmustretainrecordsofallcustomsinformationrequested
andreleasedtoexterna lorganizations. Recordsincludethenameoftherequester,thedatethe
requestwasreceived,thepurposeforwhichcustomsinformationisrequired,thenatureofthe
informationdisclosedandtherationaleforthedecisiontaken.Theauditfoundthatcompliance
withthispolicyislacking.Ofthe14RIOswhoconfirmedtheirinvolvementinverbalexchanges
withtheU.S., fewerthan50%recordsuchdisclosuresinallcases.
3.45 TheauditteamfoundthatwhereafileonaU.S.request forinformationexistsinthe
CBSA’sIntelligenceManagementSystem(IMS),anotationoftheverbaldisclosureisgenerally
capturedinthesystem. However,theadministrativeactiontakenwithrespecttootherverbal
exchangesofpersonalinformationwherenocorrespondingIMSfileexistsvariedamongthe
respondents.Someindicatedthattheverbalexchangewouldberecordedintheirnotebookor
onaProvisionAccessandUseofCustomsInformationReport(CBSAFormE675).Others
respondedthatthedecisiontorecordwoulddependuponthetypeofinformationthatwas
provided.Namechecks,travellerpassagequeriesandgeneralseizureinformationwerecited
ase xamplesofthetypeofexchangethatwouldnotberecorded. TheremainingRIOsreported
thatnorecordoftheverbalexchangewouldberetained.
3.46 Rega rdingthelandbordercrossingsthatwevisited,fiveofthesixcustomsinspectors
whohavesharedtheresultsofnameand/orlanecheckswiththeU.S.reportedthatthese
disclosuresareno tgenerallydocumented. Insummary,ourauditfoundthatverbaldisclosures
ofpersonalinformationtotheU.S.arenotbeingrecordedonaconsistentbasis.

20
3.47 ThelevelofdetailinwhichverbalexchangesarereportedintheIntelligence
ManagementSystem(IMS)andofficernotebooksisanarearequiringattention.Theaudit
indicatedthattheIMSornotebookentriesdidnot alwaysrecordthenameoftheofficial
requestingtheinformation,thepurposeforwhichthe informationwasrequestedortheexact
natureofthedisclosure,i.e.,thespecificinformation thatwasreleasedinresponsetothe
request.
3.48 Itshouldbenotedthatourobservationsrelatingtorecordsofverbalexchangesof
informationarebasedonthelimitedsamplingofnotebookandIMSentriesthatCBSAprovided
forourexamination.Giventhesizeofthesample,wecannotsaywhetherapervasive,
systematicproblemexists.However,ourauditworkdidprovideastrongindicationthatthe
mannerinwhichexchangesarerecordedneedsimprovement. Withoutadequatereporting,the
CBSAcannotobjectivelyassesswhetheritstransborderinformationsharingactivitiesrespect
individualprivacyrights.
3.49 Wehaveconcludedthatwithoutproperrecordkeeping,itisnotpossiblefortheCBSAto
eitherfullymeasuretheextenttowhichinformationsharingoccurs,orassesswhetheritis
appropriateinallcases. Moreove r,intheabsenceofrecords,individualscannotexercisetheir
rightofaccesstopersonalinformationundersection12(1)ofthePrivacyAct.
Recommendation#2:
ItisrecommendedthattheCBSAformulateanactionplantoaddressverbalexchanges
ofpersonalinformation.Suchaplanshouldconsider:
● determiningtheextenttowhichcustomsinformationisbeingsharedverballywith
UnitedStatescustomsauthoritiesandimplementmea surestoensurethatall
disclosuresconsistentlycomplywithgoverningagreementsandpolicies;
● implementingmeasurestoensurethatalldisclosuresofpersonalinformationare
recordedasrequiredunderCBSApolicy;
● issuingacommuniquétoallstaffregardingtheapprovalprocessgoverning
disclosuresundersubsection107(8)oftheCustomsAct,andreinforcethepolicy
requirementsbyincludingaspecificmoduleinthedeliveryofSection107and
PrivacyActtrainingsessions;and
● monitoringcompliancewithpoliciesgoverningcrossborderexchangesofdatato
ensurethatadequatemanagementcontrolsareinplacetoprotectpersonal
informationfromunauthorizeddisclosure.
CBSAResponse:
CBSAagreeswith therecommendationandwillcreateanactionplantoreviewour
existingpracticesandguidelinesconcern ingtheuse,accesstoanddisclosureof
custo msinformation.Wewillcreatestandardsandtoolsforreportingdisclosureactivity
thatwillreflectbothoperationalrequirementsandrecommendedpracticesarticulatedby
thePrivacyCommissioner.TheCBSAsupportsthenewguidelineswithtargeted
trainingandawarenessseminarsandwillmonitortheimplementationoftherevised
direction. Further,wewillreviewrelevanttrainingmaterialsforthePOERT(former
CIRTP)trainingprogramstoensurenewstaffunderstandPrivacyrelatedrequirements
relatedtotheuse,accesstoanddisclosureofcustomsinformation.Wew illworkto
enhanceourcapacitytomonitorthecomplianceoftheguidelines.

21
TheCBSAcannot,withareasonabledegreeofcertainty,reporteitherontheextentto
whichitsharespersonalinformationwiththeUnitedStates,orhowmuchandhowoften
itdoesso. Furthermore,theCBSAcannotbecertainthatallofitsinformationsharing
activityispermittedundersection107oftheCustomsActandSection8ofthePrivacy
Act.
3.50 ToassesstheextenttowhichitsinformationsharingactivitieswiththeUnitedStates
complywiththePrivacyAct,theCustomsActandthebilateralagreementsbetweenthetwo
countries,theCBSAmusthavethecapacitytotrackalltransborderexchangesof pe rsonal
information. Thiscapacityissignificantlyunderdevelopedatthepresenttime.
3.51 Oneoftheobjectivesofthisauditwastoreportandmap,totheextentpractical,what
informationaboutCanadianstheCBSAtransmitstotheUnitedStates,howthisisdoneand
forwhatpurposes.Initialinquiriesweredirectedatestablishingwhatreferencematerialthe
CBSAhadthatwouldassistinthisregard,includingdataflowdiagramsandprogram
descriptions.Inadditiontoproviding recordsoutliningtheautomatedexchangeoflookoutsand
advancepassengerinformation,theCBSAprovidedachartthatcaptured,ingeneralterms,the
informationsharingprocess–thatis,thelegalauthorityforsharing,nameoftheinternational
agreement,thetypeofinformation sha red(e.g.,informationrequiredtoenforcecustomslaws)
andthemodeoftransmission(writtenorelectronic).
3.52 WhilethetaskofmappingdataflowsforthesharedlookoutandHRTIinitiativescanbe
accomplishedwithrelativeease,suchisnotthecasefortheotherongoingexchangesbetween
CanadianandU.S.customsauthoritiesattheregionallevel.
3.53 Asreportedearlier,anumberofthesedisclosuresareverbalandunrecorded. Furthe r,
wefoundthatdocumentationofverbaldisclosuresisdispersedamongvariouslocationssuch
asofficers’notebooksandelectronicf ilesandarenoteasilyiden tifiedasretaininginformation
thathasbeenexchangedacrossthe CanadaU.S.border.Thissituationpreventedusfrom
using arandomsampleapproachinconductingfilereviews. Instead,asnotedpreviously,the
auditteamhadtorelyuponCBSApersonneltoidentifyfilesforexamination,moreorlessfrom
the irrecollectionofspecificcases.Onceidentified,thenotationsrelatingtoverbalexchangesin
anumberofthesefilesdidnotclearlyindicatewhatinformationhadbeensentacrossthe
borderandforwhatspecificpurpose.
3.54 WithoutacorporatemechanismforrecordingalldetailsoftheAgency’stransborder
dataflowsofpersonalinformation,theCBSAhaslimitedabilitytomeasureitslevelof
compliancewiththelegislativeandpolicyframeworkgoverningthesharingofinformationwith
foreigngovernmentsortheirinstitutions.Moreover,CBSAmanagementcannotobtainafull
accountingofwhatpersonalinformationisbeingexchangedandtheextentoftheexchanges.
Furthermore,managementcannotprovidethisinformationtoothers–suchasParliament,the
PrivacyCommissionerandtheCanadianpublic.

22
Recommendation#3:
ItisrecommendedthattheCBSAimplementwaysandmeansofcapturingalltrans
borderdataexchangesforprogrammanagementandaccountabilitypurposes.This
mightinclude–butisnotlimitedto–theconstructionofdataflowdiagrams,
modificationstoexistinginformation systemstoreliablyrecordandidentifyallsharing
activitieswithforeigngovernments.
CBSAResponse:
CBSAagreeswith therecommendation,andacknowledgesthatwewillneedtofurther
documentpreferreddisclosurepractices. Thisworkcanformpartoftheplanto
strengthenourplannedPrivacyManagementFramework. Wewillconsiderguidelinesto
strengthenproceduresdesignedtodocumentdisclosureandensureappropriate
managementaccountabilityforthecompliancewithguidelinesontheuse,accesstoand
disclosureofcustomsinformation. WewillworktoensureallBranchesandRegionsare
familiarwithrevisedguidelinesandpreferredprocesses. Ourintentionisthatthe
guidelineswillreflectboththetermsandconditionsofourlegislativeauthorityandalso
reflectiveofgenerallyacceptedprivacyprinciples.
Additionally,suchtransborderdataexchangeswillbeidentifiedanddescribedin
narrativeanddiagrammaticaldocumentation,andsystemaudittrailswillbeincorporated
intoITsystemstoidentifyandlogsha ringactivitieswithforeigngovernments.
TheCBSAaudittrailstrategyiscurrentlyunderdevelopmentandtheframewo rkwillbe
completedbyDecember2006inordertoensurerequiredaudittrailsandlogsharing
activitiesarepartofourSoftwareDevelopmentLifecycle(SDLC)forprojectsand
systems.

23
INTEGRATEDCUSTOMSENFORCEMENTSYSTEM (ICES)
Back ground
3.55 Gove rnmentdepartmentsandagencieslargelydependoninformationdatabases,
programs,andnetworkstocarryouttheirrespectivemandates.Asthepersonalinformation
undertheCBSA’scontrolresidesprimarilyinelectronicdatabases,ourauditincludedreviewing
andassessingthecontrolsofkeyITsystems. Thesecontrolsarecriticaltoensuringthat
personalinformationisadequatelyprotected.Vulnerabledatamakenotonlyforpoorsecurity
butalsopoorprivacy.
3.56 TheIntegratedCustomsEnforcementSystem(ICES)isanautomatedcustoms
enforcementsupportsystem. Underthetermsof aMOU,theCBSAacquiresitsinformatics
servicesinfrastructurefromtheCanadaRevenueAgency(CRA).Thisagreementextendsthe
termsofaservicearrangementthatexistedwhen thecustomsandrevenueprogramswere
bothpartoftheformerCanadaCustomsandRevenueAgency(CCRA). TheCBSAis
responsibleforallinternalsecuritycontrolsoftheICES.
3.57 TheICESdatabaseisdesignedtosupportthefunctionsoffrontlinecustomsinspectors,
intelligenceandinvestigationspersonnelbyallowingthemtocollect,analyzeanddisseminate
informationrelatedtorisksattheborder. Italsoprovidesacommonrepositoryforcustoms
enforcementdata,e.g.,dataonarrests,seizuresandongoingcustomsinvestigations.
3.58 Customsinspectorsandintelligenceofficersareabletocreateaccess,maintainand
disseminatelookouts(seetextboxbe low)atthelocal,regional,andnationallevel. ThePrimary
AutomatedLookoutSystem(PALS)atlandbordercrossings(licenceplatereader)andthe
IntegratedPrimaryInspectionLineSystem(IPIL)atairports(traveldocumentreader)willreturn
lookout,cautionandenforcementdatamatchhitsf romtheICESdatabasetocustoms
inspectors. Thesystem’soperationalreportsprovidetransactionleveldetailsonlookouts,
seizuresandpassagehistoryofindividualsandconveyancesatbordersandairports.
A“lookout”isanelectronicfilerecordcreatedintheICES.Thelookoutflagsoridentifies
particulartravellersorvehiclesaccordingtovariousriskindicatorsorotheravailable
intelligence.
Personalinformation
3.59 Allinformationpertainingtoanenforcementactiontakenagainstanindividualor
businessisenteredintotheICESdatabase. Thepersonalinformationretainedthereinwould
typicallyinclude,amongotherthings:
thereason(s)theindividualwasreferredtosecondaryscreening;
the resultsofthesearchandnotesofinterviewsconductedduringthesecondary
examination;
tombstonedata–name,age,address,citizenship,licencenumbe r,passport
number;
theenforcementactionstaken(individualwassearched,arrested,detained,
etc.)andtheresultsoftheinquiry;
the identityoftravelco mpanions.

24
3.60 Otherdetailsrelatedtoconveyances,commodities,methodsofconcealmen tand
indicatorsarealsoreported.Customsinspectorscanautomaticallyreceiveinformationonan
individualthroughanautomatedpreviousoffenderquerythatcapturespreviousseizuresor
custo mswarningsassociatedwithagivenperson.
FlowofPersonalInformation
Source:CBSAdescriptionoftheIntegratedCustomsEnforcementSystem(ICES)–January21,2005
Notes:
WiththeexceptionoftheCanadianPoliceInformationCentre(CPIC)databank,
allprogramsindicatedaboveareunderthecontroloftheCBSA.
Trafficrefersprimarilytononcommercialtravellers,whichwasthefocusofthe
audit. Whilenotreflectedintheabovediagram,thetrafficiconalsoincludesthe
IPILsystem–utilizedtoprocessairtravellersarrivinginCanada.
AdjudicationsreferstoappealsfromadministrativedecisionsundertheCustoms
Act,anareathatwasnotexaminedaspartofthisaudit.
ADJUDICATIONS
ADJUDICATIONS
CPICQ UERY
CPICQ UERY
RCMP
RCMP
PALS/TEPS/ICES
PALS/TEPS/ICES
EXECUTIVEREPORT ING
EXECUTIVEREPORT ING
District,Region ,HQ
District,Region,HQ
SeizureReports
SeizureReports
Decisions
LookOuts
Look Outs
ToFront
ToFront
Line
Line
ExaminationResults
SeizureData
Intelligence
SeizureData
Statistics
Statistics
ProgramReporting
ProgramReporting
Intelligence
Intelligence
CaseTracking
CaseTrack ing
Analysis
Analysis
ICESDAT ABASE
Respon sible
Enforcement
ICESDAT ABASE
ICESDAT ABASE
Respon sible
Enforcement
INTELLIGENCE
INTELLIGENCE
INVESTIGATIONS
INVESTIGATIONS
ACRO SS/ICES
ACRO SS/ICES
Comme rc ial
Comme rcial
Traffic
Traffic
ICES
ICES
ServiceandProtection
ServiceandProtection
AttheBorder
AttheBorder

25
Disclosurestoforeigngovernments
3.61 Asdescribedelsewhereinthisreport,personalinformationcollectedbytheCBSAmay
bereleasedtoforeigngovernmentsoragenciesunderMutualLegalAssistanceTreaties
(MLATs),CustomsMutualAssistanceAgreements(CMAAs),MemorandaofUnderstanding
(MOUs)orotheragreementsandarrangements.Section107(8)oftheCustomsActprovides
thelegislativeauthorityforsuchdisclosures.
3.62 OnMarch9,2005,theCBSAandtheU.S.CustomsandBorderProtectionAgency
signedaMOUtofacilitatetheAutomatedExchangeofLookoutsandtheExchangeofAdvance
PassengerInformation(API).TheNationalRiskAssessmentCentre(NRAC)–examinedas
partofthisaudit–andtheU.S.NationalTargetingCentre(NTC)jointlymanagetheinitiative.
3.63 Whenintelligenceofficers,intelligenceanalystsandotherauthorizedCBSAemployees
createalookout,theyhavetheoptionofsharingthelookoutwiththeUnitedStates. Ifalookout
isselectedforsharing,itisforwardedelectronicallytotheNRACforreview. Afte rconfirming
thatthelookoutmeetsthecriteriaforsharing,itistransmittedelectronicallyf romtheICES
applicationtotheU.S.TreasuryEnforcementCommunicationsSystem(TECS). Oncethis
transmissionhasbeencompleted,thelookoutisaccessibletoU.S.customsauthoritiesatports
ofentry.
3.64 Ourreviewevaluatedthecontrolsinplacetosafeguardtheintegrityofpersonal
informationthattheCBSAmanageswithintheICESsharedlookoutprogram.TheITreviewof
controlsovertheICESdatabaserelatedirectlytotheCBSA’sobligationsundersections4to8
ofthePrivacyAct.Theauditfocusedontheprivacyandsecurityprotectionsfortheuse,
disclosureandintegrityoflookoutda tastoredwithintheCBSAITinfrastructure,aswellasthe
transmissionofsha redlookoutdatabetweentheCBSAandtheU.S. Wea lsoreviewedthe
logicalandphysicalsecurityoverpersonalinformation,ITchangemanagement,and operations
ITcontrols.TheauditteamconsideredthefollowingICESactivitiesduringtheexamination:
· crossborderexchangeofsharedlookouts;and
· specificITsecuritycontrolsfortheICES.
3.65 OurITauditoftheICESdatabasewasconductedintandemwiththeauditexamination
oftheNationalRiskAssessmentCentre’ssharedlookou tandHRTIinitiatives. Itshouldbe
notedthatourauditdidnotincludeanevaluationoftheITcontrolenvironmentutilizedbythe
U.S.NTCtoprotectinformationon cetheCBSAhastransmittedittotheU.S.
TheIntegratedCustomsEnforce mentSystem(ICES)SecurityArchitectureiswell
designed.
3.66 Thearchitectureofthesystemreferstothemainframecomputerandserversaswellas
allcommunicationlinks,f irewallsanddefinedsecurityzonesintendedprimarilytoprotectthe
systemanditscontentsfromexterna lattacks. WelldefinedandconstructedITarchitecture
providesthefoundationforothersecurityandprivacyenhancingITcontrols.

26
3.67 WefoundthatthesecurityarchitecturesurroundingtheICESapplicationandsystemsis
welldesigned.ItprovidesseveraltypesofprotectionateverycriticalITlevelandacentral
controloveraccessbetweencontrolledzones.
3.68 TheMOUbetweenCanadaandtheU.S.coveringtheexchangeoflookoutinformation
requirestheCBSAandU.S.CustomsandBorderProtectiontorespecteachother’sexpiration,
cancellationandmodificationstolookouts.However,theMOUcontainsfewdetailsaboutthe
specificITcontrolsthatareusedtoprotectpersonalinformationwithintheU.S.Treasu ry
EnforcementCommunicationsSystem(TECS).Asnotedabove,ourauditdidnotevaluatethe
controlsforprotectingthisinformationonceithasbeentransmittedtotheU.S.However,we
seeopportunitiesforimprovingthebilateralcontrolf ramework.
Recommendation#4:
ItisrecommendedthattheCBSAworkwithitsU.S.counterpartstoprovidemutual
levelsofassurancethatrespectiveITsecuritycontrolsareadequatetoprotectthe
privacyofcitizendatainsharedlookouts.Inthisregard,specificconsiderationcouldbe
giventoextendingServiceLevelAgreementstoincludedescriptionsoftheprocessesto
deleteshareddatauponexpiryorcancellation,andthe requirementforregularprivacy
andsecurityaudits.
CBSAResponse:
TheresponsibilityofourU.S.counterpartstoprotecttheprivacyofcitizendatainthe
sharedlookoutsisintegraltotheMOUsignedbetweentheCBSAandtheUnitedStates
CustomsandBorderProtection(USCBP)fortheAutomatedExchangeofLookoutsand
theExchangeofAdvancePassengerInformation(API).TheU.S.hasalsoputinplacea
processforthedeletionofexpiredand/orcancelledlookouts.
AreviewofthecurrentSLA’swillbeundertakenandimprovementswillbemadetothe
bilate ralcontrolframeworkbyDecember2006.
UnitedStatescustomsauthoritiesdonothavedirectaccesstotheICES.
3.69 OurauditconfirmedthattheICESapplicationdoesnotpermitU.S.authoritiestoaccess
personalinformationdirectly. ElectroniccommunicationsbetweenCanadaandtheU.S.are
performedasa“push”ratherthana“pull”,withtheCBSAprovidingselectedlookoutinformation
totheU.S.aftertheCBSAhasverif iedthattheinformationcanbeshared.
3.70 TheexchangesbetweentheICESandTECSsystemsareencryptedwithapproved
algo rithmsusinghardwarecryptographicdevicestoprotectdataintegrityintransit.Failureof
the sedevicesismonitored.
Printingoflookoutdataisnotlogged.
3.71 UserlogsareITreportsaboutusers’activitiesinaparticularsystem. Theyareretained
inthesystemandcanbeprintedforverificationpurposes. TheselogsincludeuserIDsand
computeridentif ication,aswellasfilenumbersthathavebeenaccessed,modifiedordeleted
withdateandtime. Logsareimportantaudittools fortracingtheactivitiesofindividualuserson
anongoingoradhocbasis. Loggingtheseactivitiesiskeytodeterminingwhetheraccess
rightshavebeenappropriatelyexercisedaccordingtotheneedtoknowprinciple.Userlogs–

27
andtheiruseasatoolformonitoringandauditingpurposes–arenecessarytoensurethe
integrityofprograminformationandtoensurethatuseanddisclosureoftheinformationisin
compliancewithprivacyprinciplesando rganizationalpolicies. However,users(employees)
shouldbeinformed,throughnoticesandsecuritypolicies,thatthesecontrolproceduresexist.
Accesstosuchlogsmustbestrictlycontrolledtopreventinappropriateuseanddisclosure.
3.72 WhiletheICESlogsallactivitiesconductedwiththeapplication,itdoesnotlogthe
printingoflookoutdatathatmaycontainpersonalinformation. Thispresentsapossibleavenue
fordisclosureofpersonalinformation,eitherthroughaccidentormaliciousintent,withoutan
audittrailorhistorytotrackandidentifythesourceofthedisclosurebacktoanindividualuser.
Recommendation#5:
ItisrecommendedthattheCBSAmodifytheICESapplicationtoensurethatthelogging
capacityincludeswhenanICESprintoutismade.
CBSAResponse:
AtthepresenttimethefollowingmessageappearsbeforeanylookoutisprintedinICES
Inadditiontotheprintwarningprovided,allCBSAsystemsincludeageneralwarningat
thetimeoflogonthattheuseofsystemsisforauthorizedusersandofficialbusiness.
RequiredinformationwillbeincorporatedintoICESaudittrailaspartoftheCBSAaudit
trailstrategyandimplementedintotheICESsystembyDecember2006.

28
TheCBSA’sITChangeManagementFrameworkiswelldefined.
3.73 ChangemanagementintheITcontextisasystematicapproachtoadaptingto,
controllingandintroducingchangestoaparticularITsystem,soanorganizationcanaddress
anynewoperationalrequirementsofthatsystem.Changemanagementreliesondeveloping
procedures,controls,technologyandsoftwaretomodifyIThardwareandsoftwareprograms.
Effectivechangemanagementisessentialtopreservinganorganizat ion’sdataassets,
improvingprogramdeliveryandprotectingtheintegrityofpersonalinformationusedforits
decisionmakingprocesses.
3.74 TheauditfoundthattheCBSA–alongwiththeCRA–hadawelldefinedandcontrolled
changemanagementframeworkandprocessfordesigning,developingandtestingnewIT
requirements.Thisprocessfollowsanapprovedindustrystandardprocess forincorporatingIT
changes,including:
· changesandupgradestoapplicationfunctionality;
· databasechangesandupgrades;
· changestotransactionvolumes;and
· operatingsystempatches.
3.75 Thechangemanagementtestingprocessallowsforthesafetestingofamigrationplan
fortheanticipatedchangesinaseparatetestenvironment,withoutriskofnegativelyaffecting
thecurrentoperatingsystem/programortheintegrityofitsinformationholdings.
3.76 TheCBSA’steamapproachtochangemanagementprovidesabroaderskillsetand
betterchecksandbalancestoensuretheintegrityofchangesandprogramcodethanifone
personwereresponsibleforsuchmajorchanges.Thisapproachalsohelpstomitigatethe
riskofaccidentalormaliciousITchangesortheinsertionof“backdoors”intoprogramming
codethatcouldaffecttheconfidentialityandintegrityofdataprocessedandstoredbytheICES
application. Asanaddedprecaution,theCBSAdoesnotallowITprogramdeveloperstohave
accesstothefinalproductionenvironment.
3.77 TheCRArequiresallchangestotheICESenvironmentstopassthrougha22person
committee,whichmeetsonaweeklybasis. Anychangerequiresfivesignaturesbeforeitcan
beimplemented.WhenchangesarerequiredtothedataintheICESdatabase,aprocessof
authorizationsisfollowedandchangesarelogged.
3.78 OurinquiriesdididentifyanumberofminorissuesforCBSA’sconsideration.
Specifically,threeDatabaseAdministratorsintheCBSAhavetheprivilegestomakeICES
databasechanges.Newdatabasestaffmustbetrainedandmustdemonstratetheirabilityto
performchangesbeforebeinggivenanydBAaccess.Wenotedonlyoneinstanceduringa
databasechangewherebackoutprocedureswerenotfollowedbecausetheyweretechnically
notpossible.
3.79 We alsonoted thattheCBSAlacksdocumentedproceduresforremovingaserver
fromproductionandpreproductionenvironmentsandprovidingappropriatecontrolsover
conf identialityandintegrityofdataontheserver.Again,onlyoneinstanceofthissituationhad
beennotedandappropriatestepsweretakentosaf eguardtheassets.

29
ITrolesandresponsibilitiesneedtobeclearlydefined.
3.80 ItisimportantthatvariousITrolesandresponsibilitiesbeclearlydescribedand
communicatedtoallparties.ClarityinthisareaiscentraltoeffectivelymanagingthemanyIT
securitycontrolsrequiredtoprotectcustomsandpe rsonalinformationacrossorganizations
(CBSAandCRA),programsandgeographicareas.Th istaskwouldincludedefiningleadership
roles(i.e.,oftheDepartmentalSecurityOfficerandInformationTechnologySecurityOfficer)as
wellasfunctionalITmanagers,specialistsandusers.
3.81 Atthetimeoftheaudit,theCBSAlackedupdatedorganizationalchartsandcontact
liststodocumentrolesandresponsibilitiesunderitsnewITsecurityfra mework. Thisisan
underlyingproblemwithanumberoftheITcontrolcategoriesandreflectstheCBSA’sfairly
recentcreationasanindependentorganization.
3.82 OurauditfoundthatsecurityroleswithintheCBSAarehighlydistributedtosupportthe
specificneedsofeachprogramandapplication.Theriskofthisdecentralizedcontrolstructure
isthattheremaybeinconsistencyinthewayeachprogramareacomplieswithcommon
standards,policiesandtrainingrequirements. Anymajordivergencefrombaselinestandards
maycreateaweaklinkintheAgency’ssecuritychain. Anyweaknessinthechaincouldleadto
securitybreachesandcompromisepersonalinformation.
3.83 We notethattheCBSAandtheCRAhavesignedMemorandaofUnderstandingand
ServiceLevelAgreementsthatdefinetherolesandlevelsofserviceexpectations–includ ing
securityexpectations–betweentheorganizations.
Recommendation#6:
ItisrecommendedthattheCBSAestablishandcommunicatetherolesand
responsibilitiesofalldesignatedITofficialsintheorganization,includingupdatingjob
descriptionsandorganizationalcharts.
CBSAResponse:
CBSAiscurrentlyreviewingandclarifyingtheITrolesandresponsibilities.Significant
progresshasalreadybeenmadeincla rifyinganddefiningtherolesandresponsibilities
withrespecttoITSecurityandtheDSO. Theseresponsibilitiesarealsoalignedwiththe
TBSoperationalstandardforMITS,includingthegovernanceandstructureof
organizations.Clarifiedrolesandresponsibilitieswillbeinplaceandcommunicatedby
December2006.
TheCBSAiscreatingasecuritymanagementframework.
3.84 TheCBSAcreatedtheDepartmentalSecurityOfficer(DSO)roleandorganizationin
2004.TheDSOhasbeenrecentlychargedwithdevelopingandimplementingacohesive
securitymanagementframeworkforcoordinatingallaspectsofsecuritythroughouttheAgency.

30
3.85 Thisframeworkshouldprovidethenecessarytools,methodsandstructuresfor
implementingasecuritynetworkfromoneprogramareatoanother,coveringallaspectsof
securityfortheCBSA,includinginformationalsecurityandprivacy.Itshouldalsoprovidethe
Agencywithastrongerbasisforensuringthatnooneareaofsecuritycontrolbecomesthe
weaklinkthatcouldunderminetheorganization’sentiresecurityframework.Inourview,a
keycomponentoftheframeworkwouldbeanevaluationtoassesstheeffectivenessofthe
frameworkinprotectingpersonalinformation.
Recommendation#7:
ItisrecommendedthattheCBSAcontinueitseffortsto createacohesivesecurity
managementframework.Itshouldauditthisframeworkwithinayea rofits
implementationtoensurethatitisoperatingefficientlytoprotectcustomsand
personalinformation. WealsorequestthattheCBSAprovidetheresultsofthisauditto
theOfficeofthePrivacyCommissionerofCanada.
CBSAResponse:
TheCBSAintendstohaveacompletesecuritymanagementframeworkimplementedby
theendoffiscal2007. Thefeasibilityofanauditorpostimplementationreviewwillbe
consideredatthattime. Privacy relatedresultsarisingfromanauditorreview
conductedonthesecuritymanagementframeworkwillbesharedwiththeOfficeofthe
PrivacyCommissioner.
Acce ssrightstotheICESareinkeepingwiththeneedtoknowprinciple.
3.86 ControlledaccessrightstoanITsystemanditsvariousdataelementsrepresentakey
safeguardbecausetheyrestricttheuseanddisclosureofpersonalinformationtothose
individualswithalegitimateneed. Aneffectivemethodofmitigatingtheriskofinappropriate
useanddisclosureofpersonalinformationistolimitaccessrightstothesystemtoasmall
numberofusers.
3.87 ThecreationofnewICESuserprofilesistightlycontrolledthroughprocesseswithinthe
operationalunitsandtheITHelpDesk.OnlythosewithaneedtoknowreceiveaccesstoICES
information,andonlyatthelevelnecessaryfortheirjobpositionanddefinedfunctions.
3.88 Thecreationofuserprofilesissupportedthroughauseraccountrequestformthat
mustbesignedbytheuserandauthorizedbytheindividual’smanager. Bysigningtheuser
requestform,theindividualacceptsresponsibilityformaintainingtheconfidentialityofthedata.
Arecentchangealsorequiresuserstoacknowledgethattheyshouldno tsharetheiruserprofile
orpassword.Thelevelofaccessrequiredbytheuserisassignedandverifiedbythe
individual’smanagerbeforebeingsenttotheITHelpDesk,whereauserprofileiscreated
andtheindividual’saccessrightsareactivated.
3.89 Wewereadvisedthatnewusersreceivesomesecurityawarenesstrainingfromtheir
respectiveprogrammanagers. Thistrainingemphasizestheneedtomaintaintheconfidentiality
ofinformationobtainedfromtheICESdatabase. Italsocoversprocedu resformanaging
accounts/passwordstopreventnon usersfromobtainingaccesstothesystem.

31
3.90 Tohelpmanageuserprofilesandaccountsingeneral,arecentCRAprojectwas
implementedtocontinuallyreviewtheneedforPrivilegedUserRiskManagementSystem
(PURM)accountsintheCRAandtheCBSA. Thepurposeoftheprojectistoimproveboththe
integrityofuseraccountassignmentsandpasswordstrength/managementcommensuratewith
theusers’roles. Theuseofeffectivepasswordmanagementpoliciesensuresthatpasswords
arechangedfrequently,arenotreusedandaresoconstructedastoavoiddetection.Recent
upgradestotheproprietaryActiveDirectorySystemwithintheCBSAandCRAwillalsoassistin
properlymanaginguseraccountsattheorganizationallevel.
3.91 AlthoughaccesstotheICESdatabaseisgenerallywellcontrolled,theprocessfor
requestingaudittrailinformationwas,untilrecently,maintainedbythesameofficialswho
reviewedtheaudittrails. TheCBSAhastakencorrectiveactiontoremedythissituationand
hasassignedtheresponsibilitiesformaintainingandmonitoringaudittrailstoseparate
individuals.Wealsonotedthatatthetimeoftheaudit,theICESdatabasemanageraccounts
werenotmonitoredoraudited.
Recommendation#8:
ItisrecommendedthattheCBSAlogandmonitordatabaseadministrators’accessto
andtheoperationsperformedontheICESdatabase.
CBSAResponse:
CBSAhasreviewedtheproceduresandprocessesforloggingandmonitoringtheICES
databaseadministrator’saccessandimplementedadditionalcontrolmeasures. The
CBSA’saudittrailstrategywillfurtherimproveauditcapabilitiesontheICESsystemby
December2006.

32
PASSENGERINFORMATIONSYSTEM(PAXIS)
Back ground
3.92 ThePassengerInformationSystem(PAXIS)isadatabank,applicationandITsystem
thattheCBSAusestosupportitsriskmanagementstrategyforscreeningmillionsofair
travellersenteringCanadaannually. Itwasdevelopedandimplementedin200203tomanage
advancepassengerinformation/passengernamerecord(API/PNR)data–seetextboxunder
“Personalinformation”,below–thatitreceivesfromairlines,travelagentsandautomatedticket
systems.TheCBSAhasannouncedplanstoextendtheuseofthePAXISapplicationtoother
modesoftransportationinthefuture.
3.93 ThelegalauthorityforcollectingAPI/PNRinformationisderivedfromtheCustomsAct
andtheImmigrationandRefugeeProtectionActandRegulations. TheCCRA’sPassenger
Information(Customs)Regulationsprescribethatcommercialcarriersandcharters,travel
agents,andownersandoperatorsofareservationsystemarerequiredtoprovidetheMinister
ofNationalRevenue(nowCBSA)with,orprovideaccessto,specifiedpersonalinformation
onallpassengersandcrewmembersenroutetoCanadaatthetimeofthecommercial
conveyance’sdeparture.
3.94 TheCBSAusesthePAXISdatabanktostoreAPI/PNRdataonpassengersandcrew
oninternationalflightsdestinedforCanada,beforetheyarrivehere. Thesystemfacilitates
automatedqueriesbetweenAPIreceivedfromairlinedeparturesystems,withinformation
retainedonCBSAandCitizenshipandImmigrationCanadaenforcementdatabanks–e.g.,
previouscustomsinf ractionsandindividualswhoarethesubjectofacriminalorimmigration
warrant.
3.95 ThePAXISapplication facilitatesthematchingofAPIandPNRdataonsomeorall
passengersonselectedflightsforfurthe rriskanalysisbytheCBSA’sPassengerTargeting
Units(PTUs).TheseunitsarelocatedateightairportsinCanada.PNRinformationisvalidated
bythePTUsagainstvariousenforcementandintelligencesourcestoassesstheriskposedby
selectedtravellers.Basedonthisassessment,anelectronic“lookout”maybecreated,which
generallyresultsinthetravellerundergoingasecondaryexamination.
3.96 Thedataacquisitionsystem(DAS)forAPI/PNRinformationistheiDetectmessaging
softwaretoolprovidedbyathirdparty,theSociétéInternationaledeTransportAéronautique
(SITA),undercontractwiththeCCRA(nowCBSA). Thistoolcontinuestoresideonthe
CanadaRevenueAgency’sITnetwork.SITAisalsoresponsibleforprovidingthesecure
transmissionoftravellerdatafromairlinesandtravelagentstothePAXISdatabank.
3.97 TheCBSAbegantocollectAPIelectronicallyfromthefirstgroupofairline sonOctober
7,2002.BytheendofJanuary2003,theAgencywasreceivingAPIdatafromabout70%ofair
carriers. TheCBSAindicatedthat100%ofcommercialcarrierscurrentlyprovideAPIdata. We
noted,however,thattheAgencydoesnotalwaysreceiveallAPIdataelements foreveryflight.

33
3.98 TheAgencybegantocollectPNRinformationfromaircarriersonJuly8,2003. The
quantityandqualityofPNRdatathattheCBSAreceivesremainsproblematic. Inresponse
todataqualityissuesidentifiedinthepostimplementationreviewofthe PAXISapplication,a
dataanalysisfunction wasestablishedtomonitorandanalysetheseproblems.TheCBSA
continuestoworkwithindividualairlinestodevelopandimplementsolutions.
Personalinformation
3.99 API/PNRinformationconsistsofvariousdataelementsasshowninthetextbox. All
travellersandcrewmembersarrivinginCanadabycommercialaircarriersareaffe cted bythis
initiative.
API/PNRDATAELEMENTS
AdvancePassengerInformation(AP I)
APIiscontainedwithinthemachinereadablezone(MRZ)portionofapassenger’soracrew
member’straveldocuments(e.g.,passport,permanentresidentcard).TheAPIdataelements
includetheindividual’sfullname,dateofbirth,gender,citizenshipornationalityandtraveldocument
number. TheAPIthatappearsinthePAXISdatabasedoesnot includecitizenshipandnationality.
Itdoes,however,includethetraveldocument’scountryoforigin.
PassengerNameRecord(PNR)
PNRinformationincludespersonaldatarelatedtothetraveller’sreservationandtravelitineraryas
containedinacommercialcarrier’sreservationsystem.Thespecificdataelementsarelistedbelow:
PNRlocatorcode Travelagency Seatinformation
Dateofreservation Travelagent One waytickets
Datesofintendedtravel Split/dividedPNRinformation AnycollectedAPI
PassengerName Ticketinginformation Standby
OthernamesonPNR Ticketnumber Checkininformation
Allformsofpaymentinformation Seatnumber
BillingAddress Dateofticketissuance
Contacttelephonenu mbers Noshowinformation
AlltravelitineraryforspecificPNR Bagtagnumbe rs(baggageinformation)
Frequentflyerinformation Goshowinformation
Flowofpersonalinformation
3.100 Thefollowingstepsillustratetheflowofpersonalinformationforpassengersonatypical
internationalflighttoCanada.
· AtravellerbooksaflighttoCanadathroughatravelagent,arepresentative,anairline,
ordirectlythroughawebbasedbookingsystem.

34
· Thebookingagentobta insrelevantinformationandcreatesaPassengerNameRecord
(PNR)basedontheinformationprovidedbythepassenger.
· ThePNRistransferred fromthebookingagenttotheairline’sDepartureControlSystem
(DCS).
· Whenthetravellerchecksin,theairlinecounteragentcapturestheAdvancePassenger
Information(API)dataalongwiththe baggageandseatassignmentandissuesa
boardingpass.
· Theupdateddataelementsareenteredintothetraveller’sexistingrecordintheDCS.
· Aftertheaircrafthasdeparted,theairlineDCStransmitstheAPIandPNRdatatothe
PAXISdatabaseintheCBSA.
· TheAPI/PNRdatareceivedbytheCBSAisverifiedagainstenforcementand
intelligencedatabaseinformationandisriskscoredtodeterminewhetherthetraveller
shouldbesubjectedtofurtherreview.
· Ifthetravellerisidentifiedforfurtherreview,alookoutisissuedintheICESandlinked
totheIntegratedPrimaryInspectionLine(IPIL)systemusedbyfrontlinecustoms
inspectorsatairports.
· Uponarrivalattheprimaryinspectionline,theindividual’straveldocument(passport)
isscannedontheIPILcardreaderortheinformation isenteredintothesystem
manuallybythecustomsinspector.
· TheIPILsystemqueriescustomsandimmigrationdatabasesforlookoutsandifamatch
isdetected,thetravellerisreferredforsecondaryscree ning.
· Wherethesubjectofalookoutisintercepted,theresultsofthesecondaryscreening
processarecommunicatedtotheofficerwhoissuedthelookoutbywayofanelectronic
noteorinspectionreport.
· Wewouldalsonotethatirrespectiveofindividualswhoarethesubjectoflookout
notices,othertravellersmaybereferredforsecondaryscreening,withtheprimary
custo msinspectorhavingdiscretioninthisregard.Referralsmayalsobemadeona
randombasis.
Releasinginformationtoforeigngovernments
3.101 ThelegalbasisforsharingAPI/PNRdataisprovidedforunderthecommitments
advancedbyCanadaandtheUnitedStatesundertheSmartBorderDeclarationand30Point
ActionPlan,section107oftheCustomsAct,theImmigrationandRefugeeProtection Act
(IRPA)RegulationsandtheMOUfortheAutomatedExchangeofLookoutsandtheExchange
ofAdvancePassengerInformation.
3.102 TheauditfoundthefollowingITcontrolsforthePAXISdatabasetobeadequate:
· ThemanagementandsecurityofthedatalinkbetweenCanadaandtheU.S.;
· accesstoCRAdatacentresandoff iceshousingPAXISinformation;
· datamanagementwithinPAXIS;
· thecontrolssurroundingaccountsetup;and
· comprehensivetechnicaldocumentationofPAXIS.

35
NoformalizedservicelevelagreementexistsbetweentheU.S.andCanadacovering
securityandtheaccuracyofdata.
3.103 ThroughinterviewsconductedwithCBSAITstaffandmanagement,wefoundthat
althoughaMOUisinplacethatoutlinesthesharingofinformationbetweenCanadaandthe
UnitedStates,thereisnoformalizedservicelevelagreementbetweenthetwocountriesthat:
· specifiescommonsecuritystandards;
· def inesanacceptablelevelofdataaccuracy;and
· indicateswhoisresponsiblefortheaccuracyofdatasharedbetweenpartners.
3.104 Ifstandardsofsecurityarenotdefined,implementedandreviewed,theymaynotbe
adequatetoprotectthepersonalinformationofeitherCanadiansortravellersfromother
countries. Again,asnotedabove,ifresponsibilitiesandstandardsforensuringanacceptable
levelofdataaccuracyforpersonalinformationsharedbetweenpartnersarenotdefined,there
isariskthatinaccuratedatacouldleadtoadministrativeactionsthatcouldnegativelyaffect
individualtravellers.
Recommendation#9:
Itisrecommendedthataformalservicelevelagreementbeimplementedbetweenthe
U.S.andCanadatoincludemutuallyagreedsecuritystandards(basedonthe
Gove rnmentofCanadaMITSsecuritystandardandstandardsondataqualityand
screening)sothateachpartytakesstepstoensurethatsharedpersonalinformationis
complete,currentandaccurate.
CBSAResponse:
TheCBSAcurrentlyreviewsdatapriortodisclosingittotheU.S.toensurethatitrelates
tothetravellerpendingarrivalandthatitisapplicabletoprivacy,thirdpartyandother
legislativerequirementsas wellasprogramrequirements.
CBSAwillworkwiththeirU.S.counterpartstoestablishcomprehensiveservicelevel
agreementsthataddresstheapplicationofsufficientsecuritystandardsonallpersonal
informationsharedbetweenthetwocountries.
Inaddition,CBSAisimplementingariskmanagementframeworkthatwilladdressthe
needtoregularlyreviewpotentialvulnerabilitiestotheconfidentiality,integrity,and
availabilityofsuch information.
IndividualaccessrightstothePAXISdatabankhavenotbeenreviewedandvalidated
frequentlyenoughtoensurethattheyremainedvalid.
3.105 ManagingaccessrightsforITsystemsrequiresgoodcoordinationandcommunications
betweenusers,theirmanagers,ITandHumanResourcespersonnel.

36
3.106 The CBSAhasanITpolicythatcallsforcarryingoutreviewsofindividualaccessrigh ts
onaquarterlybasis. Ourauditfound,however,thatthereviewandvalidationofaccesslistings
withinthePAXISdatabankhadnotbeendoneonaregularbasisoverthepasttwoyears.
DocumentsthatweexaminedduringtheauditshowedthattheAgencyhadperformedareview
inApril2005,andanearlierone10monthspriorinJune2004. Wesharedtheseobservations
withtheCBSA. Sincethen,theCBSAperformedamorerecentreview,theresultsofwhich
wereprovidedtousinSeptember2005.
3.107 Wealsonotedthat therolesandresponsibilitiesrelatedtothePAXISsupportdesk,as
outlinedwithinthePAXISSupportDeskDocumentversion3.0,donotincludeguidelinesfor
revokingusers’acce sstothesystem.
3.108 Welookedatasampleofuseraccountsandcomparedthemagainsthumanresource
recordsontheindividuals. Althoughmanyaccountshadbeendeletedinthelatestquarterly
review,somehadnotbeendeletedoneyearafterusershadlefttheCBSA.
3.109 Withoutaclearlydefinedprocessforadministeringaccessrightsacrossthe
organization,includingregularreviewsofaccesslistingsandprocedurestoremoveuser
accessrightsassoonasanindividual’sjob/position/rolechanges,thereisincreased riskthat
someaccessrightswillnotreflectthecurrentrolesandresponsibilitiesofthesystem’susers.
Thereisalsoanincreasedriskofunauthorizedaccesswhenaccountsarenotdeactivatedafter
theuseraccountisnolongerrequired.
3.110 Achecklistshouldbeconsistentlyfollowedinallcases,andcouldbetriggeredbyany
ofthefollowingevents:anaccessreview;managersidentifyingachangeintheroleor
employmentstatusofoneoftheiremployees;humanresourcesofficialsidentifyingachangein
anemployee’sroleorresponsibilitiesduetoachangeinjobclassification;PAXISsupportteam
identifyingachangeinrole/responsibilitiesduetoarequestforadditionalaccess;andthe
productionofquarterlyreportsofaccesstoensureaccuracyofaccessrightsbasedonthe
needtoknowprinciple.
Recommendation#10:
Itisrecommendedthatastandardsystemrightschecklistbeused whenachangeinan
employee’sroles,responsibilitiesoremploymentstatusrequireshisorhermanagerto
evaluatewhatsystemaccessrightstheemployee needs,whatnewsystemaccess
permissionsarerequired,andwhatpermissionsshouldberevoked.
Recommendation#11:
ItisrecommendedthatthePAXISSupportDeskDocumentbeupdatedtoinclude
guidelinesforrevokingsystemaccessrights. WealsorecommendthatCBSAHuman
Resourcesrefertothechecklisttoensurethatemployeeswhochangepositions,those
onlongtermleaveandindividualswhohavelefttheorganizationhavehadtheirsystem
accessrightsreviewedandrevisedordeletedaccordingly.

37
CBSAResponsetoRecommendations#10and#11:
CBSAwillreviewcurrentprocessesandprocedureswithrespecttosystemaccess
rightsandpermissionsanddevelopachecklisttobeusedwhenthereisanychangein
employeestatus.TheimplementationofthePrivilegedUserRiskManagement(PURM)
Systemwillalsoassistinimprovingtheoverallintegrityofuseraccountassignmentand
passwords.
Auditlogmonitoringofviewing,retrievalandmodificationofthePAXISserveror
databaserelatedinformationbysystemsadministratorsisnotperformed.
3.111 ThroughinterviewingkeyITstafffromtheCBSAdatamanagementteamandtheCRA
Infrastructuregroup,wefoundthat,eventhoughauditloginformationisavailableandcanbe
retrieved,theCBSAdoesnotactivelymonitortheaccessofdatabaseadministratorsorserver
administratorswithinthePAXIS.
3.112 TheabsenceofactivemonitoringofthePAXISactivitiesofadministratorscouldresultin
unauthorizedactivityatadatabaseorserverlevel. Inaddition,sinceunusuala ctivitiesand
the irassociatedtrendsarenotmonitored,thereisariskofimproperactivityremaining
undetected,therebyhamperingtheintegrityofthesystem. Thereisanevengreaterriskifan
intruderhascompromisedthesystem,manipulatedthedataanddeletedalltracesofthe
intrusion.
Recommendation#12:
Itisrecommendedthatactivemonitoringofadministrators’accesstothePAXISserver
anddatabasebeperformedonaregularbasistoensureadequatecontrolsovertheir
useofthePAXISapplication.
CBSAResponse:
TheCBSAaudittrailstrategyiscurrentlyunderdevelopmentandtheframewo rkwillbe
completedbyDecember2006inordertoensurerequiredaudittrailsandlogsharing
activitiesarepartofourSoftwareDevelopmentLifecycle(SDLC)forprojectsand
systems. TheCBSAwillalsoreviewthecurrentproceduresandprocessesfor
monitoringadministrators’accesstothePAXISserveranddatabaseandimplement
appropriatecontrolmeasures.

38
NATIONALRISKASSESSMENTCENTRE
Programdescription
3.113 InJanuary2004,theGovernmentofCanadaestablishedtheNationalRiskAssessment
Centre(NRAC)withintheEnforcementBranchoftheCBSA.TheCentreoperatesanumberof
initiativesandprogramsthatrelatetotravellers.TheseincludetheSharedLookoutandHigh
RiskTravellerIdentification(HRTI)initiativeswiththeUnitedStates.TheBorderWatchLineis
alsooperatedbytheCentre.
3.114 ThecreationoftheNRACandtheaboveinitiativeswereinresponsetotheeventsof
September11,2001andrecommendationsoutlinedintheCustomsPlanofApril2000,which
promotedmorerelianceonintelligenceandriskbasedassessmentstoguidecustoms
enforcementactions.
3.115 Asreportedabove,theNRACisresponsibleforoperatingtheBorderWatchLine(1800
TipCallCentre). Usingatollfreetelephonenumber,membersofthepublicmayreport
informationaboutcrossbordercriminalorsuspiciousactivity.Suchcallsaredirectedtothe
appropriateCBSAregionaloperationalunitforapprop riateaction. A lthoughthecaller’sidentity
remainsconfiden tial,theinformationprovidedmaybesharedwithdomesticagenciesand
foreigncustomsorganizationsonaneedtoknowbasis,afterthereliabilityoftheinformation
hasbeenassessedbytheCBSA.
3.116 AnumberofStandardOperatingProcedures(SOPs)gove rnthedaytodayoperations
oftheNRAC.Intermsofinformationsharingactivities,alldisclosures,bothwithintheCBSA
andtoexternalorganizations,aresubjecttotherestrictionscontainedinsection107ofthe
CustomsAct,CBSApolicy,andtheCanadaUnitedStatesMOUfortheAutomatedExchangeof
LookoutsandtheExchangeofAdvancePassengerInformation.
Thesharedlookoutinitiative
Back ground
3.117 AlookoutisanelectronicfilerecordcreatedintheIntegratedCustomsEnforcement
System(ICES)forspecifictravellersorvehiclesbasedonriskindicatorsandotheravailable
intelligence. CanadaandtheUnitedStateshavebeensharing selectedlookoutsforanumber
ofyears.TheautomatedorelectronicsharingoflookoutdatabeganonFebruary6,2004.
Commercial(business)andpostallookoutsarenotsharedunderthisinitiative.
3.118 Therearethreecategoriesoflookouts. TheCBSAconsidersthecategoriesprotected
information.Generally,theyrelatetothreatstonationalsecurity,ortotheeconomicorsocial
welfareofCanada.
3.119 TheCanadaUnitedStatesMOUfortheAutomatedExchangeofLookoutsandthe
ExchangeofAdvancePassengerInformation,signedonMarch9,2005,establishesthe
frameworkfortheautomatedexchangeoflookoutinformation. Asummaryofthetermsand
conditionscontainedintheMOUisprovidedbelow:
partiesmustacknowledgereceiptofalookout;
partiesmustinformtheotherwhetherthelookoutwasacceptedorrejected;
ifalookoutisrejected,thereasonsmustbecommunicated;

39
thereceivingcountrymustcomplywithsendingcountry’srulesconcerningthe
expiry,cancellationandarchivingofthelookout;
athirdpartylookoutcannotbesharedunlessthesendingcountryreceivesprior
authorizationfromthethirdparty;
lookoutswillnotbesharedwith,orbemadeaccessibleto,unauthorized
individuals;
sharedlookoutswillbeidentifiedbyaheader;
thereceivingcountrymaynotarbitrarilycancel,modifyorchangethedatesofa
lookout;and
theresultsofexaminationsundertakenasaresultofalookoutmustbeshared
withthecountrythatissuedthelookout.
3.120 Asnotedabove,lookoutinformationisstoredintheCBSA’sIntegratedCustoms
EnforcementSystem.
Personalinformation
3.121 Lookoutdataidentifiesthesubjectaccordingtoavailableinformation.Inadditiontothe
subject’sname,dateofbirthandgender,alookoutmaycontainaphysicaldescriptionofthe
individualandotherspecificidentifyingdata.
3.122 Alookoutalsocontainsanarrativesectionthatprovidestherationaleforthelookoutand
includesinformationthatmayincreaseitseffectiveness.
3.123 SeveraltypesoflookoutsmaybesharedundertheCanadaU.S.agreement.These
includelookoutsrelatedtonationalsecuritythreatsandcrossbordercriminalactivity.
Transborderflowofpersonalinformation
3.124 ThedataflowbeginswiththeentryofalookoutbytheCBSA(normallyaregional
intelligenceofficer)ortheU.S.CustomsandBorderProtectionAgency(CBP). Alookout
enteredbytheCBSAischosenforsharingbythelookoutauthorizer(e.g.,RIO)whoisasked
ifheorshewantstosharethelookoutwiththeU.S.CBP.Thelookoutauthorizerisalsoasked
whetherthelookoutinformationisfromathirdpartysource(e.g.,policeagency)and,ifso,
whethertheyhaveobtainedpermissiontoshareit.
3.125 TheNRACisresponsibleforreviewingCBSAsharedlookoutspriortotransmissionto
the U.S. Asnotedlater(paragraph3.132),notallsharedlookoutsarereviewedbytheNRAC
beforetheyarecommunicatedtotheU.S.
3.126 LookoutsreceivedfromtheU.S.arereviewedbyNRACstafftoensurethattheymeet
establishedsharingcriteriaandcontainsuff icientinfo rmationtoenableacustomsinspectorto
correctlyactionandresponduponinterception.
3.127 Accordingtoinformationobtained fromNRACofficials,theCBSAacceptedabulk
transferofapproximately17,500records(existinglookouts)relatedtonationalsecurity fromthe
U.S.CBPinMarch2003.TheserecordswereplacedintheCanadianlookoutsystemba sedon
the iractivestatusandcategorytype.Thelookoutswereloadedwithoutpriorscreening.
Subsequenttocompletingareview,5,000ofthelookoutswereremovedfro mtheCBSA
system,leavingapproximately12,500lookouts. Thistransferofrecordswasnotpartofthe
sharedlookoutinitiative.

40
3.128 AftertheautomatedsharedlookoutinitiativewasimplementedinFebruary2004,a
secondbulktransferwascompletedtoimproveandupdatetheinformationfromtheU.S.CBP
intheCanadianlookoutsystem.Thissecondtransferwasbasedonspecificrequirementsand
replacedthepreviouslookoutrecordsreceived.Weweretoldthat4,000mettherequirements.
ThesewereindividuallyvettedbyNRACpersonnelfor,amongotherthings,qualityandpractical
use. Asaresultofthisexercise,approximately100lookoutswereremovedfromtheCanadian
system.NRACofficials furtheradvisedthattheexpirydates fortheremaininglookouts
(approximately3,900)weresetatnomorethanoneyearfromthedateoftransfer,withthe
optionofextensionasdeemednecessa ry. Wewerealsoinformedthatlessthantenofthese
lookoutsremainactivetoday.
3.129 Intermsofthelookoutsthatwereeithernotacceptedfortransferorweresubsequently
rejectedorcancelledasnotedabove,NRACofficialsexplainedthatthiswasduetothelackof
sufficientdetailtoidentifythesubject(s),quality,usefulnessorrelevancyofthelookout. A
numberofduplicatelookoutswerealsorejected.
3.130 Resultantratesareonemeansofmeasuringtheeffe ctivenessofthelookoutprogram.
TheCBSAdefines“resultants”asenforcementactionsthatoccurafteratravellerhasbeen
flaggedinalookoutandintercepted. Examplesofenforcementactionsincludearrest,seizures
ofcontraband,andthedetectionofsmuggledgoods. Alookoutmayalsobecreatedforthe
solepurposeofmonitoringanindividual’stravelpatternsandtravelcompanions.While
intelligencerelatedinterceptionsmaynotresultin anenforcementaction,theyarenevertheless
effectivefromanintelligencegatheringperspective. Further,resultantratesdonottakethe
deterrencefactoroflookoutsintoaccount. Forexample,anindividualmayavoidtravelling
acrosstheborderorrefrainfromcarryingoutcertainactivities.
NotalllookoutsaresubjecttoavettingorreviewprocessbeforetheCBSAsharesthem
withtheUnitedStates.
3.131 Theauditfoundthatanumberofregionalandheadquartersintelligenceofficialsare
authorizedtosharelookoutslocallywithU.S.authoritieswhenemergencycircumstances
exist–e.g.,animminentrisktonationalsecurity,healthorsafety.Suchlookoutsareissuedby
telephonetoaU.S.customsofficial. Theaudit foundthatnotalllocallyissuedsharedlookouts
areinresponsetoanemergencyorimminentrisk.
3.132 OneoftheNRAC’srolesistoreviewCanadianlookoutsbeforetheyaretransmittedto
the UnitedStates. Theobjectiveofthereviewistoensurethatlookoutsmeetestablished
criteriaforsharing,containsufficientinformationtobeeffe ctiveanddonotcontaininformation
thedisclosureofwhichisprohibitedunderlaw. Althoughnotappearingasasystemicissue,a
numberofregionalintelligenceofficersindicatedthattheyhaveorwouldcontacttheirU.S.
counterpartsdirectlytoissuealookoutratherthanhavingthelookoutprocessedelectronically
throughtheNRAC.Giventhatlookoutscanbesharedonarealtimebasisthroughthe
automatedexchange,itispuzzlingthattheNRACreviewprocesswouldbecircumventedwhen
emergencycircumstancesdonotexist. Inadditiontop rovidingamechanismforreviewingthe
qualityofdata,theNRAC’sinvolvementintheprocessensuresthatallsharedlookoutsare
capturedformonitoringandauditingpurposes.
Recommendation#13:
ItisrecommendedthattheCBSAinstitutemeasurestoensurethatalllookoutsshared
withtheUnitedStatesaretransmittedthroughtheNationalRiskAssessmentCentrefo r
qualitycontrol,monitoringandauditingpurposes.

41
CBSAResponse:
TheCBSAwillundertakeareviewoftheexistingprocessesforlookoutsharing. It
shouldbenotedhoweverthattheNRACandNTCexchangeislimitedtohigherrisk
lookoutcategoriesonly. NonNRACandNTCexchangestobeaddressedinActionPlan
regardingRecommendation#2.
Thepersonalidentifyinginformationonsomelookoutsislimitedtoanindividual’sname,
whichcreatesariskthatthewrongpersoncouldbesubjecttounnecessarysecondary
referralsatbordercrossings.
3.133 Attachingadateofbirthtothenameofapersonforidentificationpurposesisnota
mandatorydataelementundertheCanadaU.S.sharedlookoutinitiative.Thisfactcould
increasethenumberoftravellerswhoarereferredtosecondaryexaminationonthebasisof
nameonly. Arguably“nameonly”lookoutscouldincreasethenumberof“nomatches”orfalse
positives–anindividualwho,uponsecondaryexamination,isfoundnottobetheperson
identifiedinthelookout. Astudyandanalysisofthemethodologyusedtopositivelyidentify
individualsforlookoutsharinghasnotyetbeencarriedout.Therefore,thereremainstherisk
thatindividualsmaybedeemedahighorunknownriskbasedonminimaldata–nameon ly.
3.134 Aspartofo urexamination,werandomlyselected125lookoutsforreview.Thesample
wasextractedfro mvarioustypesoflookouts–e.g.,currency,narcotics,hatepropaganda,
liquor,kidnapping,missingchildren,generalsmuggling,terrorism. TheyincludedbothCBSA
issuedlookouts,andsharedlookoutscreatedbytheCBSAonbeha lfofotherCanadianlaw
enforcementagencies.Approximately20%ofthesamplewerelookoutsthathadbeenissued
bytheU.S.andtransmittedtoCanadaunderthesharedlookoutinitiative.
3.135 The125lookoutssampled,comprising309subjects(individuals),satisfiedthe
establishedcriteriaforsharingundertheCanadaU.S.automatedlookoutprogram. However,
wefoundoneCanadianissuedlookoutwheretheidentifyinginformationwaslimitedtothe
subject’sname. Wemadethesameobservationinanumberofcaseswheremultiplesubjects
werelistedonthelookout.Insummary,therewere16otherlookoutsthatidentified27
individualsassubjectsofinterest.Ofthese,theiden tifyinginformationfor10oftheindividuals
waslimitedtotheirname;therewasnoadditionalidentifyinginformationsuchastheperson’s
address,driver’slicencenumberordateofbirth. Thesetenindividualswereassociatedtoother
subjects,vehicles,addressesandothersourcesofinformationthatwouldlinkthemtothe
lookout. Nevertheless,thereremainsthepotentialthatareferraltosecondarymaybebasedon
nameonly.
AreviewoftheeffectivenessoftheCanadaU.S.sharedlookoutinitiativehasnotyet
beenundertaken.
3.136 ThestatisticaldatathattheCBSAprovidedtotheauditteamwouldappeartosuggest
thatthelookoutresultantrate(seeparagraph3.130abo ve)inCanadaislow. Itisnotclear
whetherthisisanacceptableorusefulrategiventhe natureandattributesofhighrisk
travellers.Moreover,thestatisticsrelatingtocancelledloo koutscannotdistinguishbetween the
lookoutsthatwerecancelledbecausetheywerenolongervalidandthosethatwerecancelled
becausetheyresultedinfalsepositives.

42
3.137 Anysystemused toidentifyhighrisktravellersonthebasisofintuition,physical
indicators,intelligenceorriskscoring–oracombinationof oneormoreoftheabove–may
resultinsomeindividualsbeingref erredtosecondaryscreeningwhoarefoundtobeoflowor
norisk. WebelieveitisintheinterestofboththeCBSAandthet ravellingpublicthatsuch
occurrencesarekepttoaminimum.
3.138 AcomprehensivereviewoftheeffectivenessoftheCanadaU.S.sharedlookout
initiativehasnotyetbeenundertaken.Therefore,itisnotknownwhethertheinitiativeproduces
betterresultsthandidpreviousmethodsoflookoutsharing.
Recommendation#14:
ItisrecommendedthattheCBSAeva luatethesharedlookoutsystemtodetermineboth
itseffectivenessinidentifyinghighrisktravellersenteringCanada,andtheextentto
whichitincreasesenforcementandintelligenceresultants,whileminimizing
unnecessaryreferralsoftravellerstosecondaryscreening.
CBSAResponse:
AnevaluationoftargetingintheCBSAwillbeinitiatedin2006,andamongotherissues
theuseoflookoutswillbeanelementofthetargetingevaluation.
HighRiskTravellerIdentification(HRTI)Initiative
Programdescription
3.139 Unde rtheCanadaU.S.SmartBorderDeclaration and30Point ActionPlan,Canada
andtheU.S.havecommittedtousingtechnology andinformation sha ringtomoreeffectively
identifyhighrisktravellers.
3.140 Atthetimeoftheaudit,theHRTIinitiativeprovidedforthesharingofAPIaswellas
lookout,enforcementandpassagehistoryonapersonbetweentheCBSAanditsU.S.
counterpart,theU.S.CBP.Morespecifically,theHRTItoolfacilitatesthesharingofAPIdata
fromtheCBSA’sPassengerInformationSystem(PAXIS)andtheU.S.AutomatedTargeting
SystemPassenge r(ATSP)systemoverasecureITlink. Wewereinformedthatthesharingof
PNRdataundertheHRTIinitiativewillnotbeginpriortoJune2006.
3.141 TheCBSA’sPAXIShastwocomponents–afrontenddataacquisitioncomponent,
andabackendanalysiscomponen t. Thefrontendacqu isitioncomponentinvolvesthe
collectionofAPIand PNRaboutairlinepassengersandcrewfromacarrier’sDepartureControl
andReservationsystem. WhentheAPIdataelementsarereceived,thesystemautomatically
retrievestherequiredPNRdataforeveryindividualontheflight.
3.142 The backendanalysiscomponentinvolvesrunningriskpatterns,jointlyestablishedby
theCBSAandtheU.S.CBP,basedonknownindicators,trendsandanalysis,againsta
traveller’sAPI/PNRinordertoestablishariskscorefo rthetraveller. Theriskpa tternsare
comprisedofvariousPNRelements,howeverthescoresandrisklevelsatt ributedtothemvary
inaccordancetothepatterntheyarea ssignedto. Theriskscoretotalisusedtoassess
whetheratravellermeetsanestablishedriskthresholdofaparticularriskpattern,whichwould
theoreticallyidentifythetravellerasanindividualwhomayrequirecloserscrutinyorwhoisof
highorunknownrisk.

43
3.143 Onceaparticularriskpatternhasbeen created,mod ificationscanbemadetoany
componentoftheriskpatternbasedontheanalysisofresultsfromtheuseofthisdataatthe
border. B oth enforcementandintelligenceinformationcantriggeramodification.
3.144 ThemanagementofdataexchangedundertheCanadaU.S.HRTIinitiativeis
establishedundertheMOUfortheAutomatedExchangeofLookoutsandtheExchangeof
AdvancePassengerInformation,signedinMarch2005 . AnumberofelementsoftheMOU
supportprivacyandsecurity,includingthefollowing:
informationisnottobeprovidedinsuchawayastoallowoneparticipanttohave
directaccesstotheinformationsystemoftheother;
accesstoinformationistobeadministeredonaneedtoknowbasis;
generalresponsibilitieswithrespecttoinformationsecurityandsafeguards,
includingtheinstitutionofauditandtrackingmechanismsarearticulatedinthe
MOU;and
anyfurtherdisseminationofdatarece ivedundertheMOUissubjecttothe“third
partyrule”,whichrequiresauthorizationfromthesendingpartypriortothe
disseminationbythereceivingparty.
PersonalInformation
3.145 ThedataelementsoftheAdvancePassengerInformation(API)andPersonalName
Record(PNR)areusedforriskscoringpurposesundertheHRTIinitiative.
3.146 APIdataelementsare:name,dateofbirth,gender,documenttype,documentnumber,
thecountrythatissuedthedocument,andthedateandestimatedtimeofarrival. P NRcaptures
informationrelatingtoapersonascontainedintheairlinecarrier’sreservationordeparture
controlrecords. AlistofallPNRdataelementsisfoundinthetextbookbelowparagraph3.99
ofthisreport.
TransborderFlowofPersonalInformation
3.147 TheflowofpersonalinformationundertheHRTIinitiativeisdescribedbelow.
· WhenAPI/PNRdataisreceivedfromcommercialaircarriersenroutetoCanada,the
dataisautomaticallyscoredagainstestablishedriskpatternsdevelopedjointlybythe
NRACandtheU.S.NationalTargetingCentre(NTC). Theriskscoringsubsystem
resideswithinthePassengerInformationSystem(PAXIS).
· Whenatravellermeetstheprescribedthreshold,thefollowingdataareautomatically
senttotheU.S.NTCtoqueryagainstitsdatabases:
theindividual’sfirstandlastname;
genderanddateofbirth;
traveldocumenttype;
traveldocumentnumber;
countryinwhichtraveldocumentwasissued;
flightdateandestimatedtimeofarrival;
theriskpatternsidentified;and
theindividual’sthresholdscore.

44
· TheNRACreviewsallinformationregardinganytravellerthatmeetsathreshold,
includingtheriskscorecalculation,API/PNRinformation,informationretainedonCBSA
databasesandanyinformationreceivedfromtheU.S.NTC.
· Basedontheinformationcollected,theNRACdetermineswhethertheestablishmentof
alookoutiswarrantedandtakesappropriateaction.
3.148 TheprocessthattheNRACfollowsinprocessinganinf ormationrequestfromtheU.S.
mirrorstheabovedescription. NRACstaffconductamanualreviewofallinformation
(enforcement,passagehistoryandlookouts)beforeitissenttotheU.S.NTCforits
consideration.
Dataexchangesdonotoccurunderthefollowingscenarios:
anAPIrecordcorrespondswithatravellerintheinformationrequest,butthereis
noassociatedPNRorDepartureControlSystem(DCS)data;or
aPNRorDCSrecordcorrespondswithatravellerintheinformationrequest,but
the reisnoassociatedAPIrecord.
TheHRTIinitiativehasnotyetbeenassessedtodetermineitseffectivenessinidentifying
highrisktravellers.
3.149 ThePrivacyActrequiresthatthecollectionofpersonalinformationshouldbelimited
tothatinformationwhichisnecessaryfortheorganizationtocarryoutitslegislativemandate.
GiventhevolumeandsensitivityofthepersonalinformationbeingexchangedbetweenCanada
andtheU.S.undertheHRTIinitiative,thereisarequirement–indeed,inourview,anobligation
–fortheCBSAtoassesswhetherthebenefitsderivedfromtheinitiat ivewarranttheintrusion
ontheprivacyofthemillionsoftravellersfromwhomAPI/PNRdataarecollected.
3.150 Atthetimeofouraudit,theCBSA’sEvaluationDirectoratehadnotconductedastudyof
theHRTIinitiativeasthephaseinvolvingtheriskasse ssmentofPNRdatahadnotyetbeen
implemented.ItisexpectedthatfullimplementationwillbecompletedbyJune2006.
3.151 Untilacomprehen siveassessmentisdone,theeffectivenessoftheHRTItoolin
increasingtherateofinterdictionandpositiveresults(e.g.,preventingtheentryofinadmissible
personsandprohibitedgoods,andcollectingusefulintelligence)remainsspeculative. In
addition,theefficacyofthedataelementsandthealgorithmusedtoprocessthedatahave
yettobevalidatedorreliabilitytested. Further,thenumberoffalsepositivesthathaveoccurred
fromoutputsgeneratedbytheHRTItoolis,todate,unknown.
3.152 TwostudiesproducedbytheCBSAconcerningtheuseofAPI/PNRdatainPassenger
TargetingUnits(PTUs)wereexaminedduringtheaudit.Thesestudiesraisedconcernsabout
the qualityandquantityofPNRdatatheAgencyhasreceivedfromcertainairlines. Ourreview
ofthesereportsandourinterviewswithofficialsinthePTUsvisitedduringtheauditproduced
anecdotalevidencethatinaccurateandincompletePNRdatamayskewtheriskscoring
process.Whilewewereinformedthatan enforcementactionwouldnotbeinitiatedsolelyon
thebasisofAPI/PNRdata,theriskremainsthatincorrectPNRdatacouldresultinatraveller
meetingtheestablishedriskthreshold.Whileafalsenegative(whereariskscoringtoolfailsto
identifyahighriskindividual)raiseslegitimatesecurityconcerns,falsepositivesareofequal
concernfromaprivacyperspective.

45
3.153 Theundertakingofacomprehensivereviewoftheautomatedriskassessmentsystem
tomeasureoutcomes,includinganyunintendedconsequencestotravellers,shouldhelp
answerthequestionofwhetherthecollection,useanddisclosureofvastamountsofpersonal
informationcanbejustifiedfrombothsecurityandprivacyperspectives.
Recommendation#15:
ItisrecommendedthattheCBSAundertakeareviewoftheHRTIinitiativeassoonas
practical,includingananalysisofspecificdataelementsusedbythea lgorithm,to
determinewhetherthesystemis:
· generatinganincreaseininterdictionrateorotherpositiveresultants;
· resultinginanincreaseinthenumberoffalsepositives;and
· producingresultsthatjustifycollectingpersonalinformationonmillionsoftravellers,
asopposedtopreviousmethodsusedtotargethighriskindividuals.
CBSAResponse:
TheHRTIinitiativeha snotyetbeenfullyimplemented.Fullimplementationis
scheduledforJune2006withanindepthpostimplementationevaluationplannedfor
thefollowingyear.ThisreviewwillexploreallaspectsoftheHRTIincludingfactorssuch
aswhatdataandanalysistechniquesgeneratepositiveresults.Untilthisreviewcanbe
undertaken,inresponsetothedataqualityissuesidentifiedinthepostimplementation
reviewofPAXIS,theCBSAhasestablishedacomprehensivedataanalysisfunctionto
monitorandanalyzeproblemswiththeaccuracyandcompletenessofpassengerdata
thathaveapotentialimpactontheefficacyoftheanalysisandtargetingactivities.
TheCBSAtakesveryseriouslyitsresponsibilityforprotectingthepersonalinformation
ofmillionsoftravellersarrivinginCanada. TheCBSAgoestoextraordinarymeansto
ensurethattheprivacyofpassengerdataisprotectedbyincreasinglydepersonalizing
theinformationsothattravellers’namesarenotvisibletoCBSAofficialswhiletheyare
carryingoutanalysisforthepurposeofidentifyingtrendsandpatternswhichmighthelp
toimprovetherateofinterdictionofhighriskindividuals.

46
PRIVACYMANAGEMENTFRAMEWORK
Back ground
3.154 Theconceptanddesignofaprivacymanagementframeworkforgovernment
departmentsandagen ciesarerelativelynew.Generally,organizationshaveyettodevelopa
comprehensiveandcohesiveframeworkformanagingthepersonalinformationthattheyhold.
Tocontributetoaddressingthisgap,thePrivacyCommissionerrecentlyrecommendedthatthe
TreasuryBoardSecretariat(TBS)deve lopamodelframeworktoguideprivacymanagementin
thefederalpublicsector(page31ofthePrivacyCommissioner’s20042005Annua lReportto
ParliamentonthePrivacyActrefers).
3.155 Generally,aPrivacyManagementFrameworkshould:
· effectivelycommunicatetheimportanceofmanagingpersonalinformationtothe
organizationandfosteracommitmenttobuildingprivacyintoprogrammanagement
activities;
· establishclearobjectivesandstandard s forthecollection,accuracy,security,use,
disclosure,transmission,access,retentionanddisposalofpersonalinformation;
· clarifyanorganization’sstructures,rolesandresponsibilitiesrelatingtoprivacy,and
provideabasisfordeterminingtheresourcesandskillsneededforachievingsound
privacymanagementpractices;
· relyonsoundriskmanagementapproaches,particularlythroughprivacyimpact
assessmentsandthreatandriskassessments;
· incorporatebestpracticesandeffectivecontrolstopromotecompliance–integratingthe
bestavailableprivacyenhancingtechnologies,andmechanismsforresolvingdisputes
effectivelyandforidentifyingandcorrectingsystemweaknessorprivacyincidents;and
· promoteaccountabilityandcontinuousimprovementofpersonalinformationhandling
practicesthrough:programreporting,auditandevaluation,continuousmonitoringof
personalinformationhandlingpractices,andtheprovisionofongoingprivacytrainingto
employees.
3.156 Thescopeofourexaminationwasnotdesignedtoeitherassesstheentirespectrumof
theCBSA’ssecurityprogramsandactivities,oridentifyspecificcasesofimproperuseorlossof
personalinformation.However,privacyconsiderationsarecloselylinkedtosecurityandthe
protectionofpersonalinformationandcanbeaffectedbysecuritygenerally. Therefore,wedid
examinetheAgency’ssecurityrelatedpoliciesandprocedures,itsprocessforreportingsecurity
incidents,andtheextenttowhichprivacybreachesarereportedinternally.

47
3.157 ThroughinterviewsandexaminingdocumentswefoundevidencethattheCBSA
generallyunderstandsprivacyandwishestoadvanceitsprivacymanagementpractices.
Mattersrelatedtoprivacyandpersonalinformationmanagementareincludedinavarietyof
CBSAdocumentsbothindraftandfinalforms. Muchofthedocumentationthatwereviewed
hadbeeneitherrecentlycreatedbytheCBSA,orinheritedfromitslegacyorganization,the
formerCanadaCustomsandRevenueAgency.Thedocumentationincluded:
· securitypoliciesandprocedures–CCRAFinance&AdministrationManual
§ identifyingclassifiedandprotectedinformationandassets
§ storage,transmittalanddisposalofsensitiveinformationandassets
§ protectionofclassifiedandprotectedinformationandassetsoutsidethe
workplace
§ personnelsecurityscreening
§ accesscontrol
§ reportingofsecurityincidents
§ accesstoAgencycomputersystems
§ ITsecuritystandardsandpractices
§ remoteaccesstoandfromAgencycomputersystems
§ TRAsforITsystems
§ securityreviewsandinspectionsofcomputersystems
§ usageofpersonalcomputersatemployeeresidences
§ logg ingandmonitoringofemployeeaccesstoclientdata
§ internalinvestigationsintoallegedorsuspectedemployeemisconduct
· policiesgoverningtheuseanddisclosureofcustomsinformation
· delegationordersfortheadministrationoftheCBSA’sobligationsundertheAccessto
InformationActandPrivacyAct
· regionaltrainingpackages,includinglearner’sguide, fordisclosureofcustoms
informationundersection107oftheCustomsAct
· privacyimpactassessmentsandthreatandriskassessmentsundertakenbytheCBSA
· memorandaofunderstandingorwrittenagreementsregardingaccesstoanduseof
informationheldunderthecontroloftheCBSA
· anewdraftguidefordevelopingwrittencollaborativearrangementswithprovinces,
territoriesandotherfederaldepartmentsandagencies.
3.158 TheCBSAalsoreliesuponTreasuryBoarddirectives,policiesandinstructionfor
ensuringcomplian cewiththePrivacyAct.Thereisalsorelianceoninformalcommunication
linksasmaybeestablishedbyindividualsoutofimmediateorlocalnecessity. Finally,wewere
alsoinformedthattheCBSAintendstodevelopitsownsetofprivacyandsecuritypoliciesand
guidelinestoreplaceandupdatetho sethatwereinheritedfromtheCCRA. Thesewilltakeinto
considerationthepracticesandneedsofprogramsforwhichtheCBSAisresponsible.

48
ThetimeisopportunefortheCBSAtodevelopandimplementaprivacymanagement
framework.
3.159 Despitetheexistenceofthedocumentationnotedabove,andthefactthattheAgency
intendstodevelopprivacypoliciesandguidelines,ourauditfoundthattheCBSAlacksa
comprehensiveandcohesiveprivacymanagementfra mework–onewhichisintegratedclosely
withoperationsacrosstheorganization.Severalimportantelementsofastrongframeworkare
eitherabsent,incompleteorneedtobeupdated.
3.160 Akeyfeatureofaprivacymanagementframeworkistheabilitytoidentify,investigate
andreportonprivacybreachesinvolvinganyallegedinappropriatecollection,use,disclosureor
disposalofpersonalinformation.Thisisanareaweexaminedandreportinmoredetail. The
informationthatweobtainedduringtheauditdidnotallowustoclearlyunderstandhowthe
CBSAidentifiesandreportsprivacybreachesacrosstheorganization. Thefollowingcaptures
what welearnedandobservedthroughinterviewswithsecurityofficialsandthroughourreview
off ilesandpolicydocumentsinrelationtoidentifyingandreportingofprivacybreaches.
· ThePresidentoftheCBSAisbriefedmonthlyonsecurityincidentsthatarereportedto
CBSAHeadquarters,aswellasanycasesinvolvingtheinvestigationofemployee
wrongdoing.
· Theexistingpoliciesandproceduresthatwereinuseforsecurityincidentreportingand
managementatthetimeofourexaminationdealprimarilywithsuchdefinedthingsas:
theft,lossordestructionofrevenue,money,seized,heldorotherassets;
abuse,threats,stalkingandassaultsagainstemployees;
suspectedoractualcompromiseofprotectedand/orclassifiedinformation;
maliciouscodesandvirusalerts/attacksoncommunicationorITsystems;
destruction,mutilation,alteration,orfalsificationofrecords;
loss,theftormisuseofidentification/accesscards,buildingpasses;and
incidentsimpactingphysicalsecurityofabuildingorfacility.
· TheCBSAhas14categoriesofsecurityincidents. NothingexistsinCBSApolicy,
proceduresandreportingformsspecifictoprivacythatdescribeshowtheAgencywould
handleoccurrencesofimpropercollection,useordisclosureofpersonalinformation
(accidentalorotherwise)byCBSAemployees.
· SincetheCBSAwascreatedinDecember2003,30SecurityIncidentReports(SIRs)
havebeenfiledwiththeSecuritySectionatCBSAHeadquarters. Wewereunableto
determinewhetherallincidentsinvolvingbreachesinthehandlingofpersonal
informationwerereportedtoHeadquartersfromtheregions.
· OftheSIRsthatwelookedat:
Fiftype rcentofthesecurityincidentsdidnotinvolvepersonalinformation.

49
Ofthe50%ofincidentsthateitherexposedpe rsonalinformationorplacedthe
informationatrisk:
fourrelatedtolostorstolencomputers,mainlylaptops(thereports
indicatethatthesecomputersmayhavecontainedpersonalinformation,
butthatonehadencryptionprotection);
twoinvolvedthelossof,orimproperaccessto,customsinspector
notebooks;
threeconcernedmaillostintransit;
threeinvolvedunauthorizedphysicalaccesstorestrictedworkareas;
tworelatedtounauthorizedITaccessthroughoneemployeesharinga
useraccountwithacolleague;and
oneincidentrelatedtoapasswordbreach.
· Wenotedsomecaseswherethesecurityincidentreportsraisedquestionsabout
whetherthecomputersmayhavecontainedsensitivecustomsorpersonalinformation,
buttheresponsestothesequestionswerenotprovidedinthenarrativeofthereport.
· WealsonotedfromourinterviewsthattheCBSAcouldnotreadilytelluseitherhow
manyemployeeswe reengagedinflexibleworkarrangements(i.e.,telework),orthe
numberandtypeofcomputerdevicesthathadbeenassignedtostaffforuseoutside
CBSApremises.Externalworkingenvironmentsinvolvingcustomsandpersonal
information,coupledwithnewtechnology(e.g.,Blackberry)raisephysical,IT,
operationalandprivacychallenges.Thesepersonaldigitalassistants(PDAs)require
uniquesafeguardstomitigaterisksthatmaynotbethesameasthoseusedina
standardworkenvironment.
3.161 Wealsofoundthat, atthetimeofouraudit,theAgencyhadnoformalinternalpolicy
def iningwhentheAccesstoInformationandPrivacyDivision(ATIP)oftheCBSAwouldor
shouldbeadvisedof:
anysecuritybrea chesandinternalwrongdoinginvestigationsthatinvolvepersonal
information,or
complaintsreceivedandaddressedbyCBSA’soperationalunits(e.g.,border
crossing,airport,etc.)fromindividualswhoallegethattheirprivacyrightswere
violated.
TheAgencyinformedusthatsuchaprocesswillbeestablishedandincludedinCBSApolicies
currentlyunderdevelopment.
3.162 Further,thenewmaterialsforprivacytrainingsessionsthatweexamineddidnotdefine
what wouldconstitutea“privacybreach”.Nordid thematerialsoutlinehowprivacybreaches
(e.g.,improperuse,disclosureorlossofpersonalinformation)wouldbeinvestigatedand
reported.

50
3.163 Asafinalnote,therehavebeennoauditsoftheCBSA ’sprocessforreportingsecurity
incidents. Accordingly,theCBSAisunabletoattesttothecompletenessandaccuracyofthis
process,andwhetheritcapturesallincidentsaffectingpersonalinformation,regardlessof
whethertheincidentwastheresultofdeliberatewrongdoing,orconsideredaccidental.
3.164 WebelievethetimeisopportunefortheCBSAtoarticulateandimplementaprivacy
managementframework. Theobjectivewouldbetoimprovethesystemsandprocessesfor
observingandstrengtheningcontroloverthecollection,use,disclosure,retentionanddisposal
ofbothpersonalinformationgenerally,andpersonalinformationthatflowsacrosstheborderto
othercountries.
3.165 IndesigningandimplementingaprivacymanagementframeworkfortheCBSA,we
suggestthattheAgencyconsider:
· designatingaChiefPrivacyOfficer(CPO)withaclearmandateandcorporateroleto
promoteprivacyawarenessandcompliancewithprivacylegislationand established
informationmanagementpractices.WhileaseniorofficialhasbeenidentifiedasCPO,
thishadnotbeenmadeofficialthroughaformaldelegationwithadefinedmandateat
thetimeofouraudit.
· creatingaCommitteeofseniormanagerstooverseethedevelopmentofaprivacy
managementframeworkandtoplan,monitorandcoordina teactionstakentostrengthen
privacypractices,includingthedevelopmentofprivacypolicies. ThisCommitteewould
alsoensurethatprivacyimpactassessments(PIAs)arecompletedwhenrequired,that
requisiteguidanceandtrainingareprovidedtoprogramareasonprivacyissues,and
variousagreementsgoverningtheexchangeofpersonalinformationarecurrentand
followedthroughouttheCBSA.
· creatingadepartmentalprivacypolicythatclearlyassignsrolesandresponsibilitiesand
identifieswhereprivacypracticeswouldbeakeyelementinevaluatingtheperfo rmance
ofemployees. Thepolicyshou ldalsoarticulateexpectationsformanagingand
controllingtransborderflowsofpersonalinformationthroughoutitslifecycle.Wenote
thata formalCBSApolicydedicatedtoprivacyhasnotyetbeenissued.
· implementingregularperformancemonitoringthroughmeanssuchasautomated
identificationandreportingofunusualITtransactions,analysisofsystemusepatterns,
andinternalprivacyaudits. Theseauditswouldbothhelptoensureconsistentpractices,
andprovideassurancetoseniormanagementthatpersonalinformationisbeing
managedincompliancewiththeCustomsAct,thePrivacyAct,andapplicableinterna l
policiesandinf ormationsharingagreements.Suchmechanismsarenotprominentor
featuredatthistime.
· providingregularandongoingtrainingsessionsontheadministrationof–and
compliancewith–thePrivacyAct.TheCBSAbeganprovidingtrainingsessionson
privacyduringou raudit. Whilenotrainingwasdeliveredduringfiscalyear20042005,
sincethattimesessionshavebeendeliveredinsixregions. TheCBSAintendsto
deliverprivacytrainingcoursesatleastonceineachregionpriortoMarch2006.With
the seeffortsandtheintroductionofanongoingtrainingstrategyandplan,thelevelof
privacyawarenessandcompliancewillundoubtedlyincrease.

51
· establishingareliableandcomprehensivesystemforcapturingprivacycomplaintsand
incidentsacrosstheCBSA(regions,portsofentryincluded)toensuretheyarereported
andremedied.
3.166 Onceaframeworkhasbeenestablished,theCBSAcanthenprioritizethe
implementationofthevariouselementsoftheframeworkanduseitasapointofreference
inguidingfuturedecisionsandactions.
3.167 WhilewerecommendthattheAgen cyestablishaprivacymanagementframework,it
shouldbenotedthatnoevidencesurfacedduringtheaudittoindicatethattheCBSAhas
mishandledpersonalinformation.Atthesametime,itmustberecognizedthatsincemany
crossborderexchangeswiththeUnitedStatesareverbal,andsincedetailedrecordsofthe
disclosureswerelacking,thereremainsanopenquestionastowhethertheCBSAismanaging
personalinformationappropriatelyinallcases.
Recommendation#16:
ItisrecommendedthattheCBSAde velopacomprehensiveprivacymanagement
frameworktailoredtoitsparticularneeds.Itshouldu setheframeworkforguiding
improvementstoprivacyrelatedpolicies,systems,proceduresandpractices.Aspartof
thise xercise,theCBSAshouldclarifyandconsolidateprivacyincidentreportingand
seekwaysofstrengtheningthemonitoringofthecollection,useanddisclosureof
personalinformationindailyoperations.
CBSAResponse:
Weagree.TheCBSAwillworkwiththeTreasuryBoardSecretariat(TBS)andtheOffice
ofthePrivacyCommissionertodeterminegapsinourPrivacyManagementFramework
andwewillwelcometheiradvice.

52
PUBLICREPORTINGOFTRANSBORDERDATAFLOWS
Back ground
3.168 AsanextensionofthereviewoftheCBSA’sactivitiesintheareaoftransborderdata
flows,weexaminedhowandtheextenttowhichtheCBSAinformsParliamentandthe
Canadianpublicoftransborderdisclosuresofpersonalinformation.
3.169 Thestudyinvolvedareviewofthefollowing:
· InfoSource
SourcesofFederalGovernmentInformation20042005
· Officialreportingdocuments:
Repo rtsonPlans&Priorities
Depa rtmentalPerformanceReports
AnnualReportstoParliament
AnnualReportsontheadministrationoftheAccessto InformationActand
PrivacyAct
· Websitedocuments
3.170 We examinedthepersonalinformationbankslistedanddescribedinInfoSource for
referencestoinformationsharingwith,ordisclosuresto,theUnitedStatesorotherforeign
entities.Turningtotheofficialreportingand Websitedocuments,weusedglobalcomputer
searchestofindreferencestoinformation“sharing”or“exchange”incontextswherethe
involvementofU.S.orotherforeignorganizationsiseitherstatedormayreasonablybe
inferred.
TheCBSAcouldimprovetheinformationinitsvehiclesforinformingCanadiansand
Parliamentaboutthetransborderreleaseofpersonalinformation.
3.171 Inessence,thepublicshouldbeabletofindadequateinformationinpubliclyavailable
documents(eitherprintorelectronic)onwhatpersonalinformationtheCBSAshareswithother
countries. However,whilewefoundsomeexceptionsamongpubliclyavailablereports,
referencestotheCBSA’sactivitiesrelatingtotheflowofdataacrossbordersarebrief. They
containlittleelaborationanddonotclearlyindicatetheextenttowhichpersonalinformationis
sharedwithothercountries. Insomeinstances,theAgencyprovidesmoreinformationonits
WebsitethaninreportstoParliamentorinInfoSource(thepublicationthatprovidesanaccount
ofthepersonalinformationheldbytheAgencyandrelatedp rograms). Ourobservationsare
summarizedbelow:

53
3.172 InfoSource
· ElevenoftheCBSA’spersonalinformationbankdescriptionsreferredtoinformationor
intelligencesharingwithforeignorganizations.Ofthese,onlythreeprovidedsignificant
detailsonthesesharingactivities.
· Thespecificforeignorganizationswithwhichinformationissharedwereidentifiedin
onlythreepersonalinformationbanks. Referencestoforeignorganizationswere
generalandnonspecificinotherinstances–e.g, “UnitedStatesauthorities,foreignlaw
enforcementandinvestigativeagencies.”
· Authoritiesforreleasinginformationtoforeigngovernmentswereidentifiedinonly
generaltermsinfiveinstancesasbeing“pursuanttoanagreementorarrangementin
ordertoconductalawfulinvestigationoradministerorenforceanylaw”.
· TherewasnoexplicitreferencetoinformationsharingwiththeUnitedStatesorother
foreigngovernmentsintheAdvancePassengerInformation/PassengerNameRecord
(API/PNR),PassengerInformationSystem(PAXIS)ortheIntegratedCustoms
EnforcementSystem(ICES)personalinformationbankdescriptions.
· TheCustomsIntelligenceRecordspersonalinformationban k(CBSAPPU015 )has
notbeenidentified fo rinclusioninthenextInfoSourcepublication.Thispersonal
informationbankretainsinformationusedbytheCBSAaswellasdomesticandforeign
lawenforcementandinvestigativeagencies.
3.173 OfficialReportingDocuments
(1) 20052006ReportonPlansandPriorities
§ Thisdocumentreferredtosharingofinformationand/orintelligencewith
foreignorganizationsunderfourrubrics. However,itcontainedlittle
elaboration,anditdidnotclearlyindicatetheextenttowhichpersonal
informationisinvolved.
(2) Depa rtmentalPerformanceReportend ingMarch31,2004
§ Thereportmentionedthesharingofinformationand/orintelligencewith
foreignorganizationsunder11rubrics.Again,therewasinsignificant
elaborationandnoclearindicationoftheextenttowhichpersonal
informationwasinvo lved. Infiveinstances,informationsharingwas
referencedinconnectionwiththeNationalRiskAssessmentCen tre
(NRAC)andtheJointPassengerAnalysisUnits(JPAU).Itshouldbe
notedthattheCanadaU.S.colocatedJPAUsarenolongeroperational.
Informationsharingisalsoreferredto,ingeneralterms,inconnection
withtheCanadaU.S.SmartBorderDeclaration.
(3) AnnualReporttoParliament20052006ReportonPlansandPriorities
§ Atthetimeoftheaudit,theCBSAhadnotyetpublishedanannualreport
toParliament.

54
(4) AccesstoInformationandPrivacyAnnualReport
§ Atthetimeoftheaudit,theCBSAhadnotyetpublishedanannualreport
onitsadministrationoftheAccesstoInformationandPrivacyActs.
3.174 CBSAWebsite
· Eightdocumentsreferredtothepracticeofsharingpersonalinformationwith foreign
governments.Onlyone–afactsheetrelatingtoAPI/PNRdataandthePAXISdata
bank–describedthepracticeinsign ificantdetail.Theotherref erenceswereincluded
onfactsheetsthatrelatetotheSmartBorderDeclaration,theNationalRiskAssessment
Centre,theFreeandSecureTrade(FAST)program,immigrationintelligence,
strengtheningcustomsexaminationsatairports,andintransitcontainertargetingat
seaports.
· WiththepossibleexceptionofthefactsheetonAPI/PNRandthePAXISda tabank,
noneofthedocumentsfoundontheCBSA’s Websiteprovidedenoughinformation
abouttransborderinformationsharingtoyieldaclearpictureaboutwhatinformationis
sharedandwhen,andforwhatpurposes.
Recommendation#17:
ItisrecommendedthattheCBSAreviewitspersonalinformationholdingstoensurethat
allpe rsonalinformationbanksarelistedinthenextpublicationofInfoSource,as
requiredpursuanttosection11ofthePrivacyAct.
Recommendation#18:
ItisfurtherrecommendedthattheCBSAexaminealldescriptionsofpersonal
informationbankstoensurethatallusesoftheinformationtherein—in cludingthetrans
bordersharingofinformationwithforeigngovernmen ts–areadequatelyreflected.
CBSAResponsestoRecommendations#17and#18:
TheCBSAwillcontinuetoworkwiththeTreasuryBoardSecretariattoensureexisting
andproposedPersonalInformationBanksaccuratelyreflectwithwhom,andwhy,we
shareinformation,includingtheworkweperformw ithourinternationalpartners.
3.175 WealsobelievethattheCBSA,inconjunctionwiththeTreasuryBoardSecretariat
andothergovernmentdepartments,shouldassessotherstrategies forbetterinforming
Parliamentandthepublicaboutthesha ringofpersonalinformationwithothercountries.
Thisassessmentshouldincludewaystoimprovetheinformationinexistingannualreporting
mechanisms.Anotherpossiblestrategymightbeaspecialgovernmentwidereportonthis
issueonaperiodicbasis(e.g.,inconjunctionwithreviewoftheAntiTerrorismAct)orthe
collectiveuseof theInfoSourcepub lication,annualreportsanddepartmentalwebsitesto
makepersonalinformationhandlingactivitiesmoretransparentandunderstandablefor
CanadiansandParliament.Transparen cysupportspublicaccountabilityandisoneofthe
10fairinformationprinciplesembod iedinthePersonalInformationProtectionandElectronic
DocumentsAct(PIPEDA).

55
3.176 Ourexaminationofthereportingoffourotherentitiesyieldedsimilarresults.It
conf irmedthattheCBSAisnottheonlyorganizationthatneedstoprovidebetterinformation
onitsactivitiesintheareaoftransborderdataflows. Accordingly,wewillalsobepursuingthe
matterwiththeTreasuryBoardSecretariat.
Recommendation#19:
ItisrecommendedthattheCBSA,inconjunctionwiththeTreasuryBoardSecretariat,
assessalternativestrategiesandmeansofbetterinformingParliamentandthepublic
aboutthesharingofpersonalinformationwithothercountries.
CBSAResponse:
TheCBSAnotesthatdepartmentalreportingoftransborderdataflowsisanissuethat
theOfficeofthePrivacyCommissionerintendstopursuewiththeTreasuryBoard
Secretariat.
TheCBSAwillindependentlyapproachtheTreasuryBoardSecretariattodiscuss
potentialstrategiesthatcouldbeusedbyourAgencyandperhapsotherfederal
agenciestoimprovetransparencysurroundingthenatureofkeyinternational
relationships,whilealsorespectingourinternationalobligationsconcerning
confidentiality.TheCBSAwillexplorew iththeTreasuryBoardanysuggestionsthe
OfficeofthePrivacyCommissionermayhaveinthisregard.
56
APPENDIXA
LISTOFRECOMMENDATIONS
CustomsEnforcement
1. ItisrecommendedthattheCBSA,aspartofstrengtheningitsprivacymanagement
framework,seektoupdateandstrengthenitspersonalinformationsharingagreements
withtheUnitedStates,includingtheestablishmentofprocessesthatprovidemutual
assurancethattransborderedpersonalinformationisaccordedappropriateprotections.
2. ItisrecommendedthattheCBSAformulateanactionplantoaddressverbalexchangesof
personalinformation. Suchaplanshouldconsider:
● determiningtheextenttowhichcustomsin formationisbeingsharedverballywith
UnitedStatescustomsauthoritiesandimplementmeasurestoensurethatall
disclosuresconsistentlycomplywithgoverningagreementsandpolicies;
● implementingmeasu restoensurethatalldisclosuresofpersonalinformationare
recordedasrequiredunderCBSApolicy;
● issuingacommuniquétoallstaffregardingtheapprovalprocessgoverning
disclosuresundersubsection107(8)oftheCustomsAct,andreinforcethepolicy
requirementsbyincludingaspecificmoduleinthedeliveryofSection107and
PrivacyActtrainingsessions;and
● monitoringcompliancewithpoliciesgoverningcrossborderexchangesofdatato
ensurethatadequatemanagementcontrolsareinplacetoprotectpersonal
informatio nfromunauth orizeddisclosure.
3. ItisrecommendedthattheCBSAimplementwaysandmeansofcapturingalltransborder
dataexchangesforprogrammanagementandaccountabilitypurposes.Thismight
include–butisnotlimitedto–theconstructionofdataflowdiagrams,modificationsto
existinginformationsystemsto reliablyrecordandidentifyallsharingactivitieswith
foreigngovernments.
IntegratedCustomsEnforcementSystem(ICES)
4. ItisrecommendedthattheCBSAworkwithitsU.S.counterpartstoprovidemu tuallevels
ofassurancethatrespectiveITsecuritycontrolsareadequatetoprotecttheprivacyof
citizendatainsharedlookouts.Inthis regard,specificconsiderationcouldbegivento
extendingServiceLevelAgreementsto includedescriptionsofthe processes todelete
shareddatauponexpiryorcancellation,andtherequirementforregularprivacyand
securityaudits.
5. ItisrecommendedthattheCBSAmodifytheICESapplicationtoensurethatthelogging
capacityincludeswhenanICESprintoutismade.

57
6. ItisrecommendedthattheCBSAestablishandcommunicatetherolesand
responsibilitiesofalldesignatedITofficialsintheorganization,includingupdatingjob
descriptionsandorganizationalcharts.
7. ItisrecommendedthattheCBSAcontinueitseffortsto createacohesivesecurity
managementframework.Itshouldauditthisframeworkwithinayearofits
implementationtoensurethatitisoperatingeffici entlytoprotectcustomsand
personalinformation. Wealsorequestth attheCBSAprovidetheresul tsofthisauditto
theOfficeofthePrivacyCommissionerofCanada.
8. ItisrecommendedthatCBSAlogandmo nitordatabaseadministrators’accesstoandthe
operationsperformedontheICESdatabase.
PassengerInformationSystem(PAXIS)
9. ItisrecommendedthataformalservicelevelagreementbeimplementedbetweentheU.S.
andCanadatoincludemu tuallyagreedsecuritystand ards(basedontheGovernmentof
CanadaMITSsecuritystandardandstandardsondataqualityandscreening)sothateach
partytakesstepstoensurethatsharedpersonalinformationiscomplete,currentand
accurate.
10. Itisrecommendedthatastandardsystemrightschecklistbeusedwhenachangein
anemployee’sroles,responsibilitiesoremploymentstatusrequireshis orhermanager
toevaluatewhatsystemaccessrightstheemployeeneeds,whatnewsystemaccess
permissionsarerequired,andwhatpermissionsshouldberevoked.
11. ItisrecommendedthatthePAXISSupportDeskDocumentbeupdatedtoinclude
guidelinesforrevokingsystemaccessrights. WealsorecommendthatCBSAHuman
Resourcesrefertothechecklist toensurethatemployeeswhochangepo sitions,thoseon
longtermleaveandindividualswhohavelefttheorganizationhavehadtheirsystem
accessrightsreviewedandrevisedordeletedaccordingly.
12. Itisrecommendedthatactivemonitoringofadministrators’accesstothePAXIS server
anddatabasebeperformedonaregularbasistoensureadequatecontrolsovertheiruse
ofthePAXISapplication.
NationalRiskAssessmentCentre(NRAC)
13. ItisrecommendedthattheCBSAinstitutemeasurestoensurethatalllookoutsshared
withtheUn itedStatesaretransmittedthroughtheNationalRiskAssessmentCentrefor
qualitycontrol,monitoringandauditingpurposes.
14. ItisrecommendedthattheCBSAevaluatethesharedlookoutsystemtodetermineboth
itseffectivenessinidentifyinghighrisktravellersenteringCanada,and theextentto
whichitincreasesenforcementandintelligence resultants,whileminimizingunnecessary
referralsoftravellerstosecondaryscreening.

58
15. ItisrecommendedthattheCBSAundertakeareviewoftheHRTI initiativeassoonas
practical,includingananalysisofspecificdataelementsusedbythealgorithm,to
determinewhetherthesystemis:
· generatinganincreaseininterdictionrateorotherpositiveresultants;
· resultinginanincreaseinthenumberoffalsepositives;and
· producingresultsthatjustifycollectingperso nalinformationonmillionsof
travellers, asopposedtopreviousmethodsusedtotargethighriskindividuals.
PrivacyManagementFramework
16. ItisrecommendedthattheCBSAdevelopacomprehensiveprivacymanagement
frameworktailored toitsparticularneeds.Itshouldusetheframeworkforguiding
improvementstoprivacyrelatedpolicies,system s,proceduresandpractices. Aspartof
thisexercise,theCBSAshouldclarifyandconsolidateprivacyincidentreportingandseek
waysofstrengtheningthemonitoringofthecollection,useanddisclosureofpersonal
informationindailyoperatio ns.
PublicReportingofCrossBorderDataFlows
17. ItisrecommendedthattheCBSAreviewitspersonalinformationholdingstoensurethat
allpersonalinformationbanksarelistedinthenextpublicationofInfoSource,asrequired
pursuanttosection11ofthePrivacyAct.
18. ItisfurtherrecommendedthattheCBSAexamine alldescriptionsofpersonalinformation
bankstoensurethatallusesoftheinformationtherein—includingthetransborder
sharingofinformationwithforeigngovernments–areadequatelyreflected.
19. ItisrecommendedthattheCBSA,inconjunctionwiththeTreasuryBoardSecretariat,
assessalternativestrategiesandmeansofbetterinformingParliamentandthepublic
aboutthesharingofpersonalinformationwithothercountries.

59
APPENDIXB
AUDITEVALUATIONCRITERIA
Theevaluationcriteriaforthisauditareprincipallyderivedfromobli gationssetoutinsections4to8
ofthePrivacyAct,theGovernmentSecurityPolicy,TreasuryBoardpolicies,guidelinesandrelated
documentsgoverningthemanagementofpersonalinformation.
Inaddition,somebestpracticescriteriahavealsobeenadaptedfromSchedule1ofthePersonal
InformationProtectionandElectronicDocumentsAct(PIPEDA).
Accountability(Principle1PIPEDA):
Criteria:
Theorganizationmustdesignateindividual(s)whowilloverseeandcoordinatetheorganization’s
activitiestoensuretheaccountabilityfortheorganization'scompliancewithallprivacyobligations.
Thoseindividualsmaydelegatespecificrolesandresponsibilitiesacrosstheorganizationforensuring
privacyandsecurityprotectionsofitspersonalinformationholdings.
Theorganizationshallusecontractualorother meanstoensurethatthirdpartiesprov ideacomparable
levelofprivacyprotectionasdoestheoriginatingorganization.
Note: Referenceismadetocriteriaforinformationsharingagreementsandcontractingout. For
informationheldbyagovernmentinstitutionthestandardwouldhavetobeasgoodasorbetter
thanthatprovidedbythePrivacyAct,GovernmentSecurityPoliciesandTBGuidelines.
Organizationsshallimplementpoliciesandpracticestogiveeffecttotheprinciples,including
implementingprocedurestoprotectpersonalinformation;establishingprocedurestoreceiveandrespond
tocomplaintsandinquiries;trainingstaffandcommunicatingtostaffinformationabouttheorganization's
policiesandpractices;anddevelopinginformationtoexplaintheorganization'spoliciesandprocedures.
Openness(Principle8PIPEDA)
Criteria:
Organizationsshallbeopenabouttheirpoliciesandpracticeswithrespecttothemanagem entof
personali nformation. Individualsshall beabl etoacquireinformationaboutanorganization's policiesand
practiceswithoutunreasonableeffort. Thisinformationshallbemadeavailableinaformthatisgenerally
understandable.
Theinformationmadeavailableshallincludethenameortitle,andtheaddress,ofthepersonwhois
accountablefortheorganization'spoliciesandpracticesandtowhomcomplaintsorinquiriescanbe
forwarded;themeansofgainingaccesstopersonalinformationheldbytheorganization;adescriptionof
thetypeofpersonalinformationheldbytheorganization,includingageneralaccountofitsuse;acopyof
anybrochuresorotherinformationthatexplaintheorganization'spolicies,standards,orcodes;andwhat
personali nformationismadeavailabletorelatedorganizations(e.g.,subsidiaries).
Note: Anorganizationmaymakeinformati ononitspoliciesandpracticesavailableinavarietyofways.
Themethodchosendependsonthenatureofitsactivitiesandotherconsiderations. For
example,anorganizationmaychoosetomakebrochuresavailableinitsplaceofbusiness,mail
informationtoindividuals,provideonlineaccess,orestablishatollfreetelephonenumber.
60
IdentifyingPurposes(Prin ciple2PIPEDA):
Criteria:
Theorganizationshalldocumentthepurpose sforwhichpersonalinformationiscollected.
Theidentifiedpurposesshouldbespecifiedatorbeforethetimeofcollectiontotheindividualfromwhom
thepersonalinformationiscollected.
Whenpersonalinformationthathasbeencollected istobeusedforapurposenotpreviouslyi dentified,
thenewpurposeshallbeidentifiedpriortouse. Unlessthenewpurposeisrequiredbylaw,t heconsent
oftheindividualisrequiredbeforeinformationcanbeusedforthatpurpose.
Personscollectingpersonalinformationshouldbeabletoexpl aintoindividualsthepurposesforwhich
theinformationisbeingcollected.
Note: Theremaybeexceptionstothisprinciple,wherethecollectionisdoneaccordingtolawand
informationprovidedtotheindividualmayresultinlessorinaccuratepersonalinformationbeing
collected.
Collectionofpersonalinfo rmation(Sections4and5ofthePrivacyAct):
Criteria:
Governmentinstitutionsshallcollectpersonalinformationonlywhenitrelatesdirectlytoan
unauthorizedprogramoractivityoftheinstitution.
Subjecttoexceptionsreferredtoinsubsection5(3)ofthePrivacyAct,governmentinstitutionsare
requiredtoinformindividualsofthepurposeforwhichtheinformationisbeingcollectedandtheintended
usestobemadeofit.
Whereverpossible,governmentinstitutionsshallcollectpersonalinformation–intendedtobeusedforan
administrativepurpose–directlyfromtheindividualtowhomitrelates.
Consent(Principle3PIPEDA)
Criteria:
Organizationsshallmakeareasonableeff orttoensurethattheindividualisadvi sedofthepurposesfor
whichtheinformationwillbeused. Tomaketheconsentmeaningful,thepurposesmustbestatedin
suchamannerthattheindividualcanreasonablyunderstandhowtheinformationwillbeusedor
disclosed.
Anindividualmaywithdrawconsentatanytime,subjecttolegalorcontractualrestrictionsand
reasonablenotice. Theorganizationshallinformtheindividualoftheimplicationsof suchwithdrawal.
LimitingCollection(Principle4PIPEDA)
Criteria:
Organizationsshallnotcollectpersonalinformationindiscriminately. Boththeamountandthetypeof
informationcollectedshallbelimitedtothatwhichisnecessarytofulfilthepurposesidentified.
Organizationsshallspecifythetypeofinformationcollectedaspartoftheirinformationhandlingpolicies
andpractices,inaccordancewiththeopennessprinciple.(Principle8ofPIPEDAalsorefers).

61
Therequirementthatpersonalinformationbecollectedbyfairandlawfulmeansisintendedtoprevent
organizationsfromcollectinginformationbymisleadingordeceivingindividualsaboutthepurposefor
whichinformationisbeingcollected. Thisrequirementimpliesthatconsentwit hrespecttocollectionmust
notbeobtainedthroughdeception.
Useofpersonalinformation(Subsection6(2),section7andsubsection9(4)ofthePrivacyAct)
Criteria:
Governmentinstitutionsshalltakeallreasonablestepstoensurethatpersonalinformationthatisusedfor
anadministrativepurposeisasaccurate,uptodateandcompleteaspossible.(Accuracy–Principle6of
PIPEDAalsorefers).
Withouttheconsentoftheindividualtowhomitrelates,personalinformationshallonlybeusedbya
governmentinstitutionforthepurposeforwhichit wascollected,orforauseconsistentwiththeoriginal
purpose,orforapurposeforwhichtheinformationmaybedisclosedwithinoroutsidetheinstitution
undersubsection8(2)ofthePrivacyAct.
Whenpersonalinformationisputtoaconsistentusethatisnotlistedinthepersonalinformationbank
descriptioninInfoSource,suchausemustbereportedtothePrivacyCommissionerandincludedinthe
nextstatementofconsistentusessetoutinInfoSource.
(SeealsoLimitinguse,disclosureandretention–Principle5PIPEDA)
Use– DataMatching(TreasuryBoardPolicyonDataMatching)
Criteria:
Governmentinstitutionsmustensurethattheirdatamatchingprogram saredesignedandconductedin
accordancewiththeprinciplesoffairinformationpracticesembodiedinthePrivacyActandincompliance
withtheTreasuryBoardPolicyonDataMatching.
Limitinguse,discl osureandretention(Principle5PIPEDA)
Criteria:
Personalinformationshallnotbeusedordisclosedforpurposesotherthanthoseforwhichitwas
collected,exceptwiththeconsentoftheindividualorasrequiredbylaw.
Organizationsshoulddevelopguidelinesandimplementprocedureswithrespecttotheretentionof
personali nformation.Theseguidelinesshouldincludeminimumandmaximumretentionperiods.
Personalinformationthathasbeenusedtomakeadecisionaboutanindividualshallberetainedlong
enoughtoallowtheindividualaccesstotheinformationafterthedecisionhasbeenmade.
Personalinformationthatisnolongerrequiredtofulfilltheidentifiedpurposesshouldbedestroyed,
erased,ormadeanonymous.
Organizationsshalldevelopguidelinesandimplementprocedurestogovernthedestructionofpersonal
information.

62
Accuracy(Principle6PIPEDA)
Criteria:
Informationshallbesufficientlyaccurate,complete,anduptodatetominimizethepossibilitythat
inappropriateinformationmaybeusedtomakeadecisionabouttheindividual.
Anorganizationshallnotroutinelyupdatepersonalinformation,unlesssuchaprocessisnecessaryto
fulfillthepurpose(s)forwhichtheinformationwascollected.
DisclosureofPersonalInformation(Section8ofthePrivacyAct)
Criteria:
Personalinformationunderthecontrolofagovernmentinstitutionshallnot,withouttheconsentofthe
individualtowhomitrelates,bedisclosedtoathirdpartyex ceptinthelimitednumberofcircumstances
establishedinsubsection8(2)ofthePrivacyAct.
Paragraph8(2)(f)ofthePrivacyActpermitsafederalgovernmentinstitutiontodisclosepersonal
informationtothegovernmentofaforeignstate,aninternationalorganizationofstatesoraninternational
organizationestablishedbythegovernmentofstates–oranyinstitutionofanysuchgovernment–for
thepurposeofadministeringanylaworcarryingoutalawfulinvestigation.
Suchdisclosuresshouldbegovernedbyawri ttencollaborativeagreementbetweenthepartieswith
appropriatedataprotectionprovisionscontainedtherein.
Disclosure–PersonalInformationSharingAgreements(Criteriadevelopedfromavarietyof
sources)
Criteria&Considerations:
1.PartiestoAgreement
Doestheagreement:
a) clearlyidentifythepublicbodies,lev elsofgovernmentorotherorganizationsinvolvedinthis
sharingorexchangeofpersonalinformation?
b) nameanythirdparty contractorsorserviceproviderswhowillhaveaccesstopersonal
information?
2.Authority
Doestheagreement:
a) definethelegalauthority–law,agreementortreatypermittingthepartiestoenterintoan
agreementforthesharingorexchangeofpersonalinformation?
b) definethelegalauthoritygoverningtherespectiveprogram/activ itiesofthepartiesrelevant
totheagreement?

63
3.Purposeofagreement
Doestheagreement:
a) identifythegeneralintentof theinformationexchange?
b) identifyiftherewillbeaonewayorreciprocalsharingofpersonalinformation?
c) identifyforeachofthepurposesorreasonsstatedintheagreement,thedataelements ora
descriptionofthepersonalinformationtobesharedorexchanged?
d) differentiatebetweenthedataelementsexchangedinareciprocalarrangementaret heparties
usingdiff erentdataelements?
e) indicatewhethercommonclientidentifiersareusedand,ifso,whatarethey?
f) identifythesourcesofthepersonalinformation?
4.Accountability
Doestheagreement:
a) specifytheresponsibilitiesofeachpartyforcarryingoutthetermsandconditionsoftheagreement
aswell asdesignatewhowithineachpartyisaccountable?
b) specifywhohaslegalcontrolofthesharedpersonali nformation?
c) indicatewhetherornotthepartieshavecommonpracticesandproceduresforcomplyingwith
variouselementsoftheagreement?
d) explainthateachpartywillberesponsibleforrespondingtorequestsforaccessto,andthe
correctionof,personali nformationundertheircontrol?
e) specifythateachpartywillberesponsiblefortheactionsofitsemployees,agentsorcontractors
withrespecttotheuse,disclosureanddispositionofthepersonalinformationthatissubjecttothe
agreementandapplicableprivacylaws?
f) specifywhetherthesharedpersonalinformationissubjecttoanyotheraccessorprivacylaws,
regulationsorguidelinesbeyondthelawsofthedisclosingparty? Note:U.S.privacylaws
generallyapplytoU.S.citizensandpermanentresidentsonly.
5.Mechanismforthesharing/exchangeofpersonalinformation
Doestheagreementdescribethe:
a) methodsorproceduresthatwillbeusedtosharethepersonalinformation?
b) levelofaccessrightstopersonalinformationoftherespectiveparties,basedontheneedtoknow
principle?
6.Obtainingconsentfromornotificationtoanyaffectedparties
Doestheagreementincludeaprovision:
a)establishinghow(orif)datasubjectsareawareofthesharingactivity?
b) thatprovidesreferencetoexceptionstotheconsentrule?
7.Useofpersonalinformation
Doestheagreement:
a) clearlyidentifywhatusesaretobemadeofpersonalinformationsharedundertheagreement?
b) containlimitationsorprohibitionsagainstsecondaryusesoftheinformationforpurposesotherthan
thoseli stedintheagreement?

64
8.Disclosuretothirdparties(includingcontractorsandsubcontractors)
Doestheagreement:
a) listthethirdpartiestowhichpersonalinformationmaybedisclosedorprovidecategoriesofthird
parties?
b) clearlydefinethepurposesandcircumstancesunderwhichpersonalinformationcanbedisclosed
tothirdpartiesaswellastheproceduresthatmustbefollowedtoeffectsuchdisclosures?
c) permitdisclosureforpurposesotherthanthosespecifiedintheagreement(e.g.,researchand
statisticalpurposesorprogramplanning,forecastingorevaluationpurposes)?
d) statethatt hetermsoftheagreementapplytoanythirdpartydisclosure,includingarequirement
thatthirdpartiescomply withthefairinformationprinciplestosafeguardpersonalinformation?
9. Accuracy
Doestheagreement:
a) identifythestepst hatwillbetakentoensurethatpersonalinformationisaccurate,completeand
uptodate?
b) containaclausethatdealswiththehandlingofrequestsforcorrection?
c) statethatthesubstanceofarequestforcorrectionshouldbecomm unicatedtothosepartiesin
receiptofdisclosedinformation?
d) containaclausestatingthatthepartiesmustverifythepersonalinformationwiththeoriginating
agencybeforeitisusedtomakeanadministrativedecisionaboutanindividual?
10.Security
Doestheagreementinclude:
a) keyadministrative,personnel,technical,ITandphysicalsafeguardsandcontrolsthatarerequired
toprotectthesecurityofthepersonalinformationshared(e.g., measurestosecurethe
transmissionof personalinformationandm easurestopreventunauthorizedaccess,useor
disclosure)?
b) doestheinformationsharingagreementestablishtherequirementforaThreatandRisk
Assessment(TRA),includinganassessmentoftheriskstothepersonalinformationthatmaybe
engenderedbythearrangement?
11.RetentionandDisposal
Doestheagreement:
a) specifyhowlongthesharedpersonalinformationistobekeptandwhethertheinformationistobe
returnedtothesourceorsecurelydestroyedbytherecipient(s)?
b) indicatewhatwillhappentothepersonalinformationexchangedupontheterminationofthe
agreement?
12.DataMatchingandDataLinkage
Doestheagreementincludeanydatamatching,linkageorprofilingactivitiescarriedoutbyeitherparty
furthertothesharingofpersonalinformation?
(Note:seeTreasuryBoardPolicyonDataMatching)

65
13.PrivacyImpactAssessment
Doestheinform ationsharingagreementdefineanewordifferentkindofarrangementforthesharing
ofpersonalinformationthatwouldrequirethecompletionofaPrivacyImpactAssessm entunder
TreasuryBoardPolicy?
14.UnauthorizedUseorDisclosure
Doestheagreement:
a) establishnotificationproceduresintheeventofdiscoveryofanunauthorizeduseordisclosure
ofthesharedpersonali nformation?
b) statethatt hepartyinbreachshouldpromptlynotif ytheotherparty?
c) specifytheconsequencesofusingordisclosingthepersonalinformationwithoutauthority?
15.Disputes
Doestheagreementoutlineaprocesstobefollowedtoresolveanydisputesrelatingtotheterm sof
theagreement?
16.Audits
Doestheagreement:
a) includeaclauseal lowingforperiodicauditsofthesharingarrangementstoensurecompliance
withthetermsoft heagreement?
b) requirethatresultsofsuchauditsbesharedwiththeotherparty?
c) referenceaudittrailtoolsandmethodstobeusedtotrackaccesstorecords,modifi cationof
recordsanddisclosures?
d) referencethePrivacyCommissioner'srighttoaccessinformationheldbyfederalgovernment
institutionsforthepurposeofconductinginvestigationsandauditsunderthePrivacyAct?
Note:theremaybeotherbodieswithsimilarstatutorypowers.
17.Amendments/RenewalandCancellation
Doestheagreementprovidefor:
a) amendment(s)andrenewalsinwritingwiththemutualagreem entoftheparties?
b) cancellationbyoneortheotherparties?
18. ChangesthataffecttheAgreement
Doestheagreementinclude:
a) anundertakingthatthepartieswillprovidewrittennotificationofanylegislative,regulatory
orpolicychangesthataffecttheagreement.
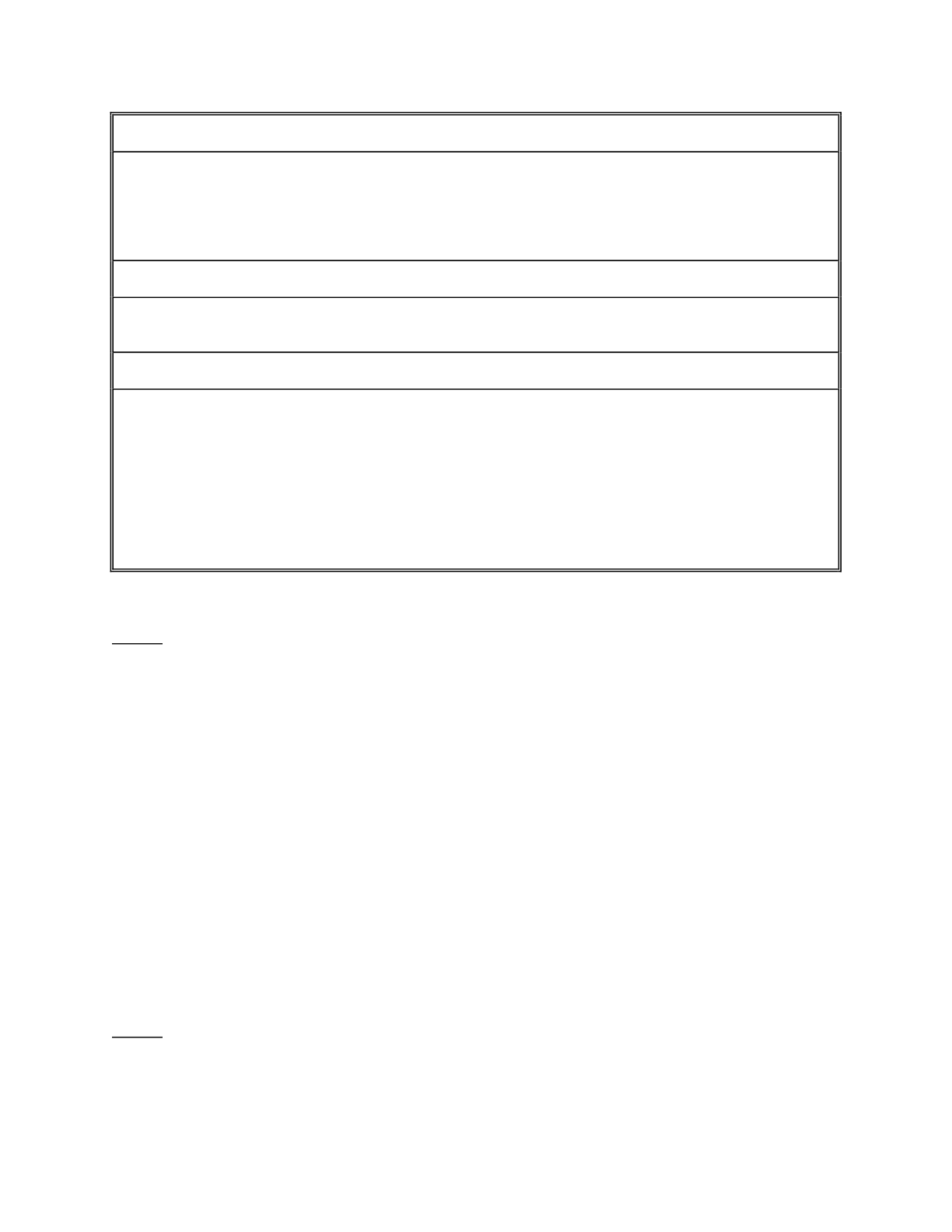
66
19.Timeframe
Doestheagreementsetoutatim eframeforits:
a) existence?
b) reviewbytheparties?
20.Definitions
Doestheagreementincludedefinitionsofanytermsthatmaybeuniquetotheagreement?
21.Signingauthorityandcontactnames
Doestheagreement:
a) haveex plicitsignoffbythe“heads”ofthepublicbodies(orbythoseofficialswithdelegated
authoritytosignsuchagreements)andbyofficialsatsimilarlevelsinotherorganizations?
b) contain:contactnames,titles,addressesandphonenumbersofappropriateofficialsofallparties
chargedwithadministeringvariousaspectsoftheagreement?
DisclosureContractingout(CriteriadevelopedbytheOPC)
Criteria:
Personalinformationwhichiscollected,used,processed,disclosed,heldordisposedofonbehalfofa
governmentinstitution,orinfulfillmentofacontractwithagovernmentinstitution,shallbemanagedin
conformitywiththepri nciplesoffairinformationpracticesembodiedinthePrivacyActandthePrivacy
Regulations.
Whenaprivatesectoragencyorcontractormanagespersonalinformationonbehalfofagovernment
institution,thecontractm ustspecifythatsuchpersonalinformationisdeemedtobeunderthecontrolof
thegovernmentinstitutionandissubjecttothePrivacyAct.
Thecontractmustalsostipulate,whereapplicable,howtheserviceproviderorcontractorwillmeetthe
Act’srequirem entsintermsofmanagingthepersonalinformationitwillhandlewhilecarryingoutthe
contract.
ThecontractshouldalsorecognizethePriv acyCommissioner’srightofaccesstothepersonal
informationforthepurposesofconductingauditsandinvesti gations.
(Foradditionalcriteria,refertoabovechecklistforPersonalInformationSharingAgreements)
SafeguardingPerson alInformation(Sections6,7and8ofthePrivacyAct)
Criteria:
Governmentinstitutionsmusthaveinplaceappropriatesecuritymeasurestoensurethat,throughoutits
lifecycle,personalinformationundertheircontrolisprotectedandnotvulnerabletounauthorizedaccess,
use,disclosure,alterationordestruction.

67
Email&Facsimiles:
Therearemanyreasonswhysendingpersonalinformationbyemailorfaxposessecurity risks.
Ifnotsentorreceivedbysecuremeans,theinformationmaybeinterceptedorexploited,or
receivedinerrorbysomeonewhoisnotauthorizedtoreceivethe information.Identifiable
personali nformationshouldnotbesentbyemailorfax,unlessbysecuremeans (.e.g.,
encryptedmessage,securefaxinasecurearea).
Governmentinstitutionsmust,therefore,adoptsecuritymeasuresthatprotecttheconfidentialnatureof
personali nformationbeingtransmittedelectronically.
Safeguards(Principle7PIPEDA)
Criteria:
Thesecuritysafeguardsmustbeadequatetoprotectpersonalinformationagainstlossortheft,aswellas
unauthorizedaccess,disclosure,use,modificationorreproduction.
Organizationsshallprotectpersonalinformationregardlessoftheformatinwhichitisheld.
Note: Thenatureofthesafeguardswillvarydependingonthesensitivityandamountofpersonal
informationcollected, itsdistribution,theformatofthedataandthemethodof storage.
Themethodsofprotectionshouldincludeadequate:physicalmeasures(e.g.,lockedfilingcabinetsand
restrictedaccesstooffices);organizationalmeasures(e.g.,securityclearancesandlimitingaccessona
needtoknowbasis);andtechnologicalsafeguards(e.g.,theuseofpasswordsandencryptiontoprotect
personali nformation).
Organizationsshallmaketheiremployees awareof theim portanceofmaintainingtheconfidentialityof
personali nformation.
Careshallbeexercisedinthedisposalordestructionofpersonalinformationtopreventunauthorized
accesstoit.
RetentionandDisposal(Subsection6(1)ofthePrivacyActandparagraphs4(1)
and(2)ofth ePrivacyAct)
Criteria:
Personalinformationmustberetainedanddisposedofinaccordancewithapprovedrecordsretention
anddisposalschedules.
Exceptasotherwi seprovidedinlaworwheretheindividualconsentstoearlierdisposal,personal
informationthathasbeenforanadministrativepurpose–thatis,inthedecisionmakingprocessthat
directlyaffectstheindividual– mustbekeptforaminimumoftwoyearsafterthelasttimeitwassoused.
Recordsshouldbeproperlydisposedofinamannerconsistentwiththeirsecurityclassification.
Access(Principle9PIPEDA)
Criteria:
Uponrequest,anorganizationshallinformanindividualwhetherornottheorganizationholdspersonal
informationabouttheindividual. Organizationsareencouragedtoindicatethesourceofthisinformation.

68
Anindividualmayberequiredtoprovidesufficientinformationtopermitanorganizationtoprovidean
accountoftheexistence,use,anddisclosureofpersonalinformation. Theinformationprovidedshallonly
beusedforthispurpose.
Inprovidinganaccountofthirdpartiestowhichithasdisclosedpersonal information,anorganization
shouldattempttobeasspecificaspossible. Whenitisnotpossibletoprov idealistoftheorganizati ons
towhichithasdisclosedinformationaboutanindividual,theorganizationshallprovidealistof
organizationstowhichitmayhavedisclosedinformationabouttheindividual.
Wherepersonalinformationhas beentransferredtoathirdpartycontractor,theorganizationmustensure
thatitobtainscopiesofrecordsrelevanttotheaccessrequestfromthethirdparty.
Wherepersonalinformationhas beendisclosedunderaninformationsharingagreement,the
organizationmustensurethatitkeepstheoriginalsforanyaccessrequestsfortheserecords.
Anorganizationshallrespondtoanindividual'srequestwit hinareasonabletimeandatminimalorno
costtot heindivi dual. Therequestedinformationshallbeprovidedormadeavailableinaformthatis
generallyunderstandable. Forexample,iftheorganizationusesabbreviationsorcodestorecord
information,anexplanationshallbeprovided.
Whenani ndividualsuccessfullydemonstratestheinaccuracyorincompletenessofpersonalinformation,
theorganizationshallam endtheinformationasrequired. Theamendmentmay involvethecorrectionor
deletionofinformation,ortheinclusionofadditionalinformati on. Whereappropriate,the amended
informationshallbetransmittedtothirdpartieshavingaccesstotheinformationatissue.
ChallengingCompliance(Principle10PIPEDA)
Criteria:
Anindividualshallbeabletoaddressachallengeconcerningcompliancewiththeaboveprinciplestothe
designatedindividualorindividualsaccountablefortheorganization'scompliance.
Organizationsshallputproceduresinplacetoreceiveandrespondtocomplaintsorinquiriesabouttheir
policiesandpracticesrelatingtothehandlingofpersonalinformation. Thecomplaintproceduresshould
beeasilyaccessibleandsimpletouse.
Organizationsshallinformindividualswhomakeinquiriesorlodgecomplaintsoftheexistenceofrelevant
redressprocedures(includingtherightof complainttotheOfficeofthePrivacyCommissionerof
Canada).
Anorganizationshallinvestigateallcomplai nts. Ifacomplaintisfoundtobejustified,theorganization
shalltakeappropriatemeasures,including,ifnecessary,amendingitspoliciesandpractices.
OTHERAUDITCRITERIA
AwarenessofthePrivacyAct
Compliancewiththespiritandspecificrequirementsofsections4to8ofthePrivacyActdependslargely
onthedegreeofunderstandingoftheAct’sprovisionsbythepersonsresponsibleforadministeringthe
Actfortheinstitutionand,toalesserdegree,byotheremployeesoftheinstitution.

69
Criteria:
Governmentemployeeshandlingpersonalinformationmustbeawareoftheirobligationsunderthe
PrivacyAct,includingrestrictionsondisclosuresofpersonalinformation.
Thegovernmentinstitutionmustprov ideem ployeeswithappropriatePrivacyActtrainingand
documentationtoensurethattheyarekeptuptodateontheirprivacyobligations.
InfoSource(Sections9,10and11ofthePrivacyAct)
Criteria:
Asacomplementtosections4to8ofthePrivacyAct,sections9,10and11oftheActrequirethatall
personali nformationholdingsmustbedescribedandpubli shedinInfoSourceasPersonalInformation
Banksorasclassesofpersonalinformation.
Governmentinstitutionsmustensurethatallsuchdescriptionsareascomplete,uptodateandaccurate
aspossible.

70
APPENDIXC
LISTOFACRONYMS
ACRONYM NAME
API
AdvancePassengerInformation
ARS
AirlineReservationSystem
CBSA
CanadaBorderServicesAgency
CBP
UnitedStatesCustomsandBorderProtectionAgency
CCRA
CanadaCustomsandRevenueAgency
CFIA
CanadianFoodInspectionAgency
CI
CustomsInspector
CIC
CitizenshipandImmigrationCanada
CIIMS
CustomsInvestigationsInformationManagementSystem
CIRTP
CustomsInspectorRecruitmentTrainingProgram
CPO
ChiefPrivacyOfficer
CMAA
CustomsMutualAssistanceAgreement
CRA
CanadaRevenueAgency
DAS
DataAcquisitionSystem
DCS
Depa rtureControlSystem
DOB
DateofBirth
DSO
Depa rtmentalSecurityOfficer
EU
EuropeanUnion
FOSS
FieldOperationalSupportSystem
HQ
Headquarters
HRTI
HighRiskTravellerIdentificationInitiative
ICES
IntegratedCustomsEnforcementSystem
IMS
IntelligenceManagementSystem
IPIL
IntegratedPrimaryInspectionLine(Airport)
IT
InformationTechnology
MLAT
Mutu alLegalAssistanceTreaty
MOU
Memoran dumofUnderstanding
MRZ
MachineReadableZone
NRAC
NationalRiskAssessmentCentre
NTC
UnitedStatesNationalTargetingCentre
ORS
OccurrenceReportingSystem
PALS
PrimaryAutomatedLookoutSystem(LandBorder)
PIA
PrivacyImpactAssessment
PAXIS
PassengerInformationSystem
PIPEDA
PersonalInformationProtectionandElectronicDocumentsAct
PTU
PassengerTargetingUnit
PURM
PrivilegedUserRiskMan agementSystem
RIO
RegionalIntelligenceOfficer
RIA
RegionalIntelligenceAnalyst
SIR
SecurityIncidentReport
TBS
TreasuryBoardSecretariat
TECS
UnitedStatesTreasuryEnforcementCommunicationsSystem
TRA
ThreatandRiskAssessment
